Understanding Common Cryptocurrency Scams
The rapid growth of digital assets has unfortunately brought a surge in cryptocurrency scams, many of which exploit user trust and familiarity with well-known crypto brands. Scammers continue to adapt, using sophisticated social engineering tactics, fake sites, and hacked accounts to deceive unsuspecting investors.
In today’s digital landscape, understanding cryptocurrency scams is crucial for anyone looking to invest in or use cryptocurrencies. These scams can take various forms, including phishing attempts, fake exchanges, and fraudulent investment schemes. Being aware of cryptocurrency scams will enable you to better protect yourself and your assets.
As you navigate the world of digital currencies, always remain vigilant against cryptocurrency scams. Knowing the signs can help you steer clear of potential losses.
Recognizing cryptocurrency scams is essential in protecting your investments and personal information. Many victims of these scams often report feeling embarrassed or deceived.
Below are six of the most prevalent cryptocurrency scams circulating online and how you can protect yourself against them.
1. Fake YouTube videos
With botted views showing known trusted people like Vitalik Buterin, Elon Musk, Bill Gates or other famous philanthropic or crypto person.
This scam relies upon those prerequisites:
Hacked Youtube account with more than 1K subs that is eligible for live streaming.
The hacked Youtube account (ATO) is renamed to SpaceX foundation, Tesla, Elon Musk, Gill Gates Foundation, Balancer exchange and so on and pushes a live stream showing recording of some real conference to add “credibility” (see above Vitalik) and a fake site gets added to the description.(above in red)
Then bots are used to generate views and this fools YouTube’s algorithms to display videos as “related” to users who are interested in crypto currencies.
They also build a fake site with the same “promotion” tied to it.
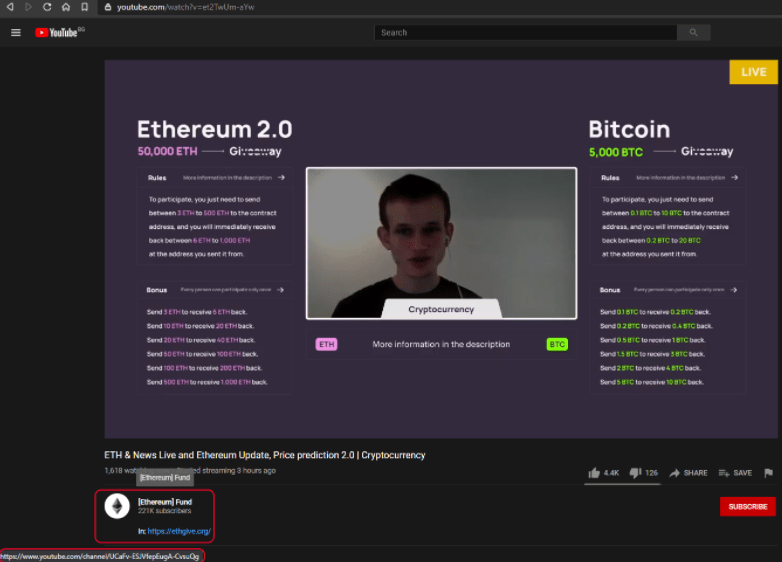
The fake sites always promises to send 1 and get 2 back, in various ways. Anything sent gets lost forever.
Scammers will also use wallets to make the scam seem more realistic.
If you see a live video promoting an airdrop proceed with caution!
Here is a neat collection of scam wallets for your viewing pleasure.
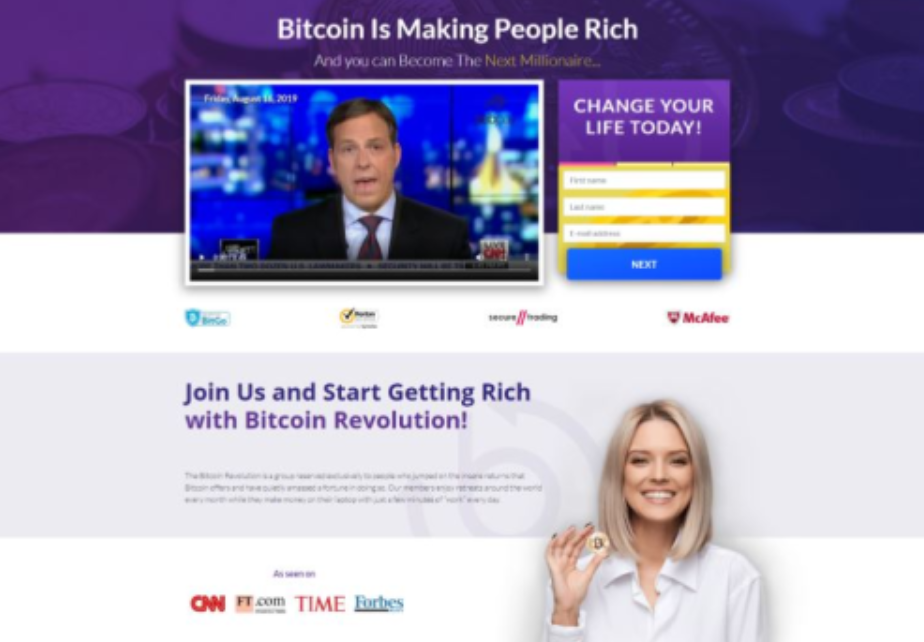
2. Bitcoin Revolution scams
Those are linked to semi legitimate businesses and often push referrals.
Another type of cryptocurrency scam involves impersonation. Scammers may create fake profiles on social media to lure in unsuspecting victims.
Additionally, it is important to be cautious of unsolicited messages promoting investment opportunities in cryptocurrency scams. Always verify the source before engaging.
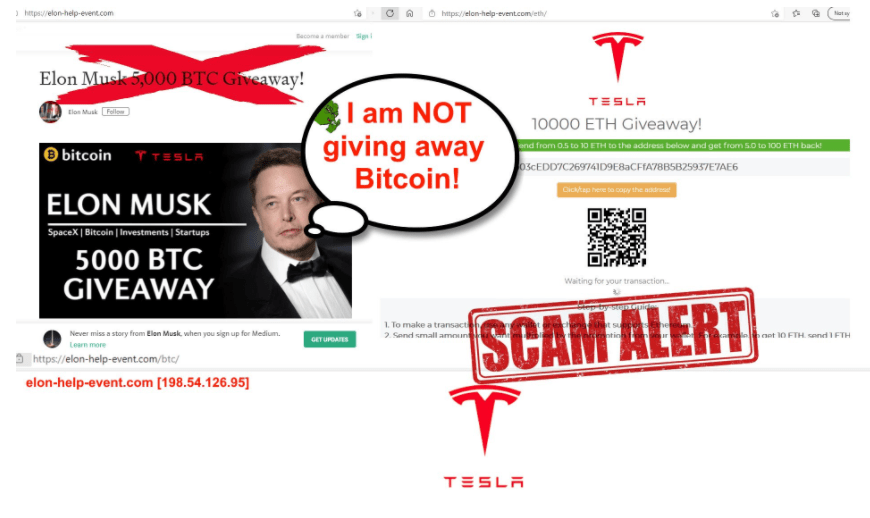
It is usually fake news article and fake video of a famous rich millionaire like Sir Richard Branson or Elon Musk and some lies about them starting the bitcoin revolution. There is often a sense of urgency asking users to sign up for the last slots. Some of them are geo-localized and if you open the site from Portugal will display a Portuguese TV host or celebrity promoting the scam, as if they were a successful investor, if page gets accessed from let’s say a Dutch IP, you will my see a Dutch famous person promoting the scam and so on.
If you sign up for those they will siphon as much money as they can, luring you that you are now bitcoin rich. but if you try to withdraw, you realize this has been a scam all along.
3. Fake exchanges and investment platforms
Staying informed about the latest trends and techniques in cryptocurrency scams is key to safeguarding your investments.
Victims of these cryptocurrency scams often report their experiences, which serve as cautionary tales for others in the community.
By learning about cryptocurrency scams, you can take proactive steps to protect your financial well-being.
3. Fake exchanges and investment platforms
They sound too good to be true. Unsolicited DM spam about fake exchange advance fee scam (you won fake money, but need to deposit real money as “verification”). The ask to register on the dummy site with throwaway email and enter the fake code. The company registration number phone and everything is usually fake. They can have real deal phones as well with fake employees, luring investors.
We recommend you to turn off direct messages to disable the ability of criminals to spam you with scams.
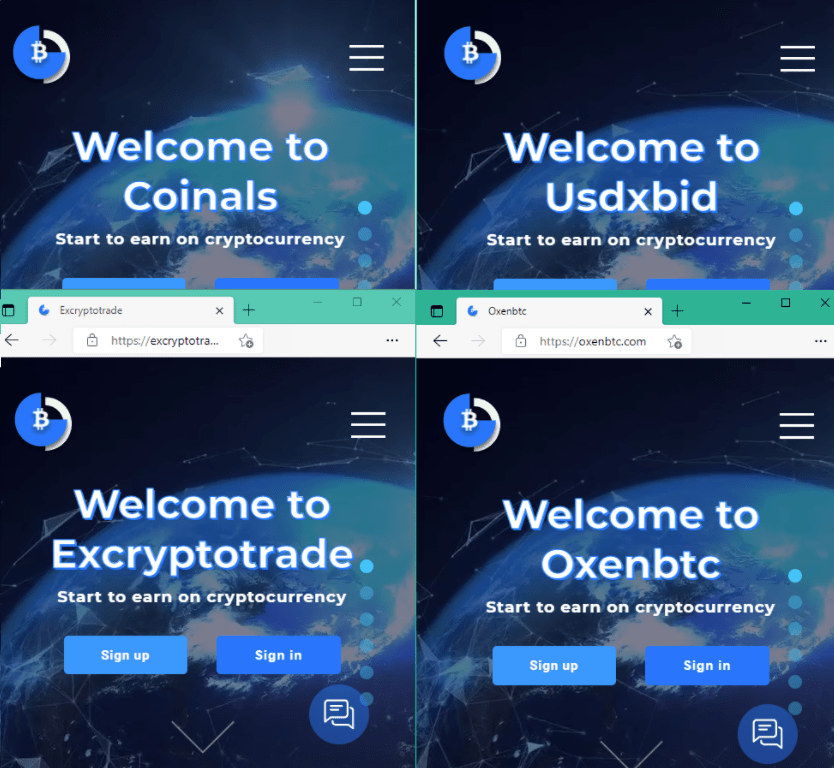 Notice the similarity between an exchange with a fake one
Notice the similarity between an exchange with a fake one
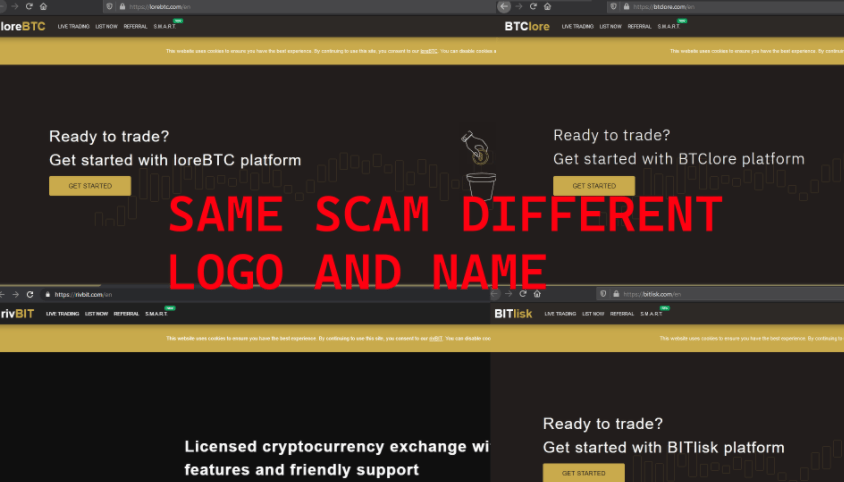 Again only the logo and name gets changed
Again only the logo and name gets changed
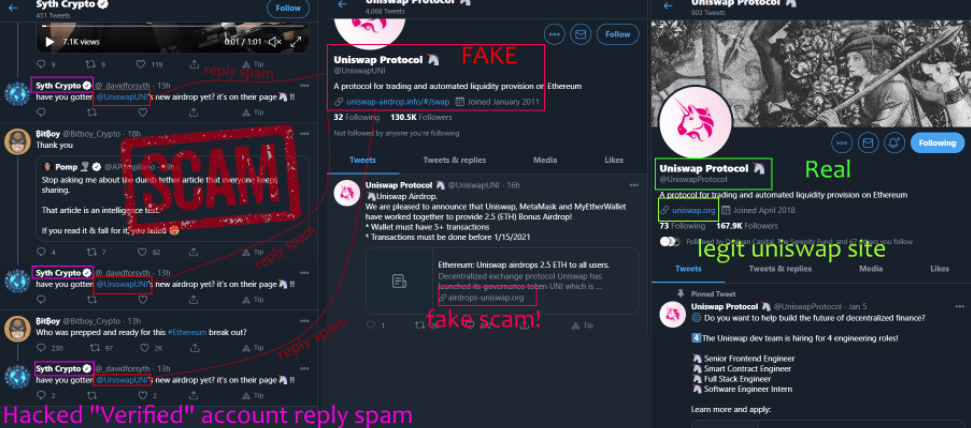
4. Twitter verified scams (fake giveaways)
Often stolen profiles get renamed to Elon Musk and start to offer “giveaways”.
They also use Reply Spam under legitimate Elon Tweets!
Fake airdrop

Scammers put videos in the replies, that appear to be as if “verified” Elon Musk typed them.
Typical twitter scam:
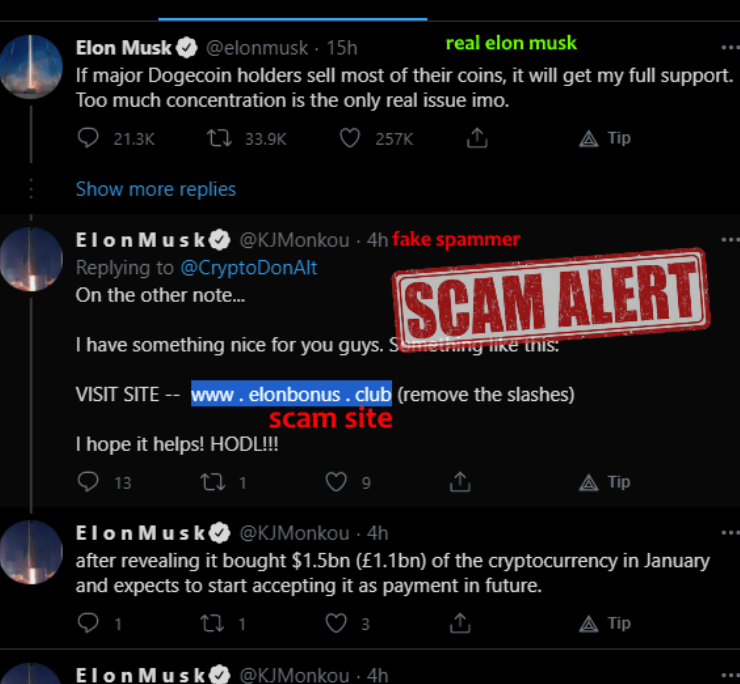
More twitter scams:
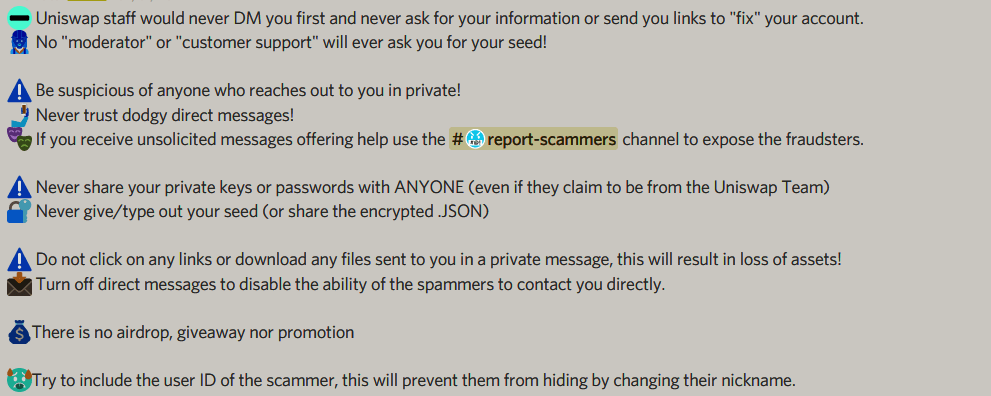
5. Discord DM unsolicited Spam
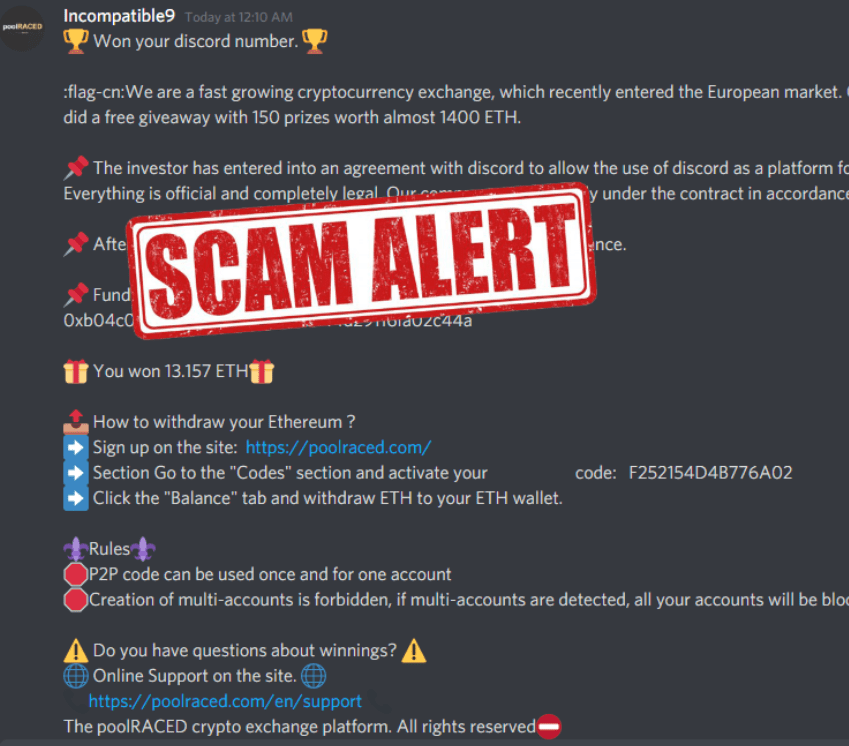
Good rule of a thumb is Staff will never DM you with an airdrop, nor will Elon Musk, Bill Gates, Coinbase, Kraken, Binance nor will the latest hot token.
All unsolicited DMs are scams!
6. Fake ICOs
NotanImaginaryDude lost $140K worth of $UNI overnight. Lets say NotanImaginaryDude sees a fancy new “farming” scheme called “UniCats”, and decides to invest some money in it. Who knows, it might be the “next YFI” (first big mistake)
Then NotanImaginaryDude decides to deposit some $UNI, and gets the trivial message “Allow this Dapp to spend your UNI” message from Metamask wallet extension.
Naturally they think “Oh sure, this again. As with all the farming Dapps do that, no worries”
⚠ And approves the transaction! (second big mistake)
NotanImaginaryDude farms some $MEOW, and happily decides “Done with this $MEOW game. I’ll pull out all my UNI and capitalize gainz now”
What NotanImaginaryDude doesn’t know though, is that once they approved the contract to use ∞ tokens, the contract can take their tokens at any time. Even after they were withdrawn from the farming scheme!
Bottom line – be careful which site you allow your metamask to interact with.
Dodgy contract that allows holder to leave investors with worthless token and drain their ETH.
This type of scam is called approval scam and is relatively newer. To check granted permissions you can use one of those tools to revoke any redundant contracts’s permissions that might have been granted previously.
etherscan.io/tokenapprovalchecker
Some threat actors also use approve infinite amount, instead of limited.
Anybody can create a rug pull token or copycat token or a bogus token with hidden functions. This is the double edged sword of true decentralization.
If those 4000% seemed to good to be true, it is probably because it is a fake token with artificial volumes, designed to lure naïve “investors”.
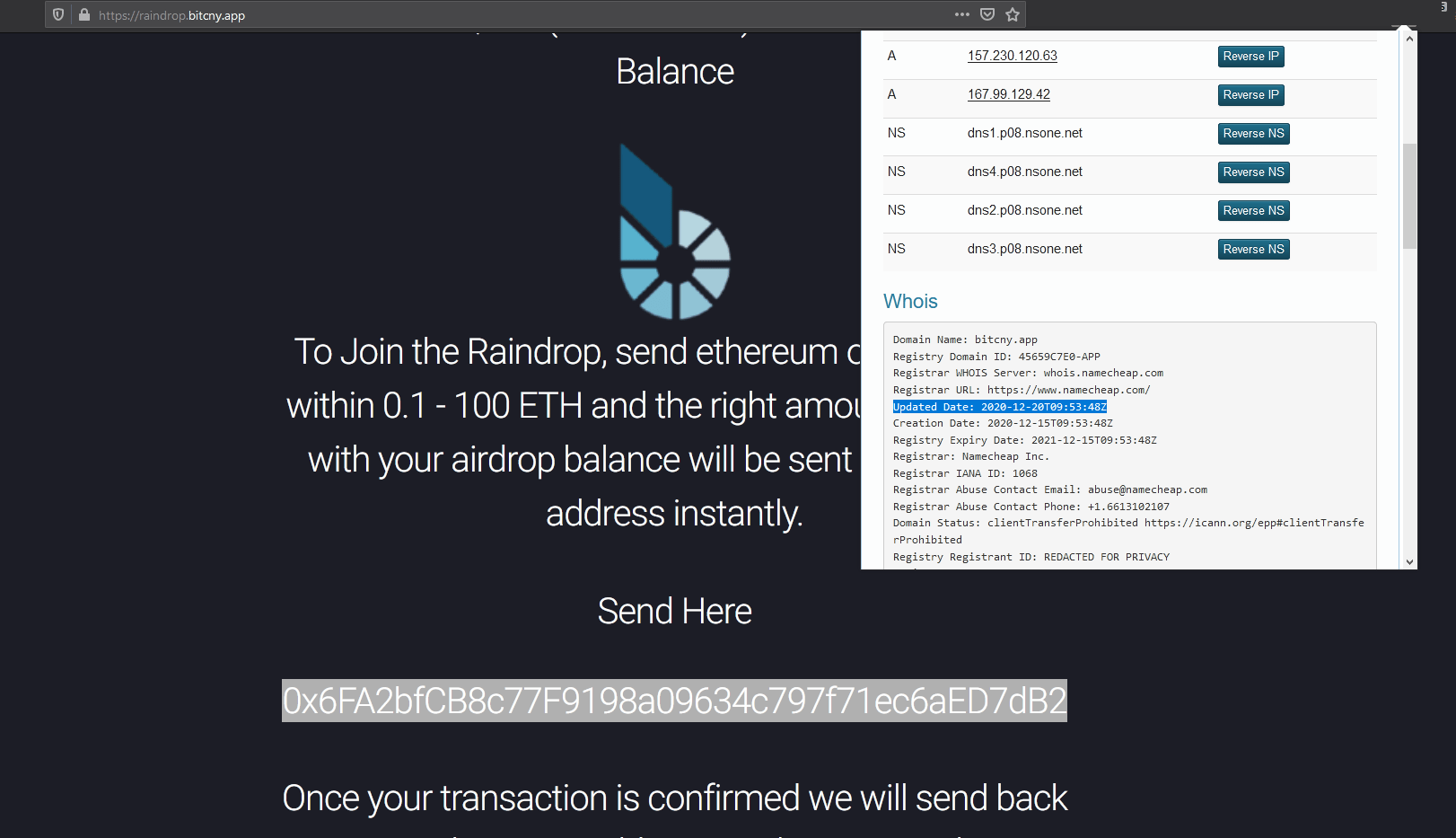
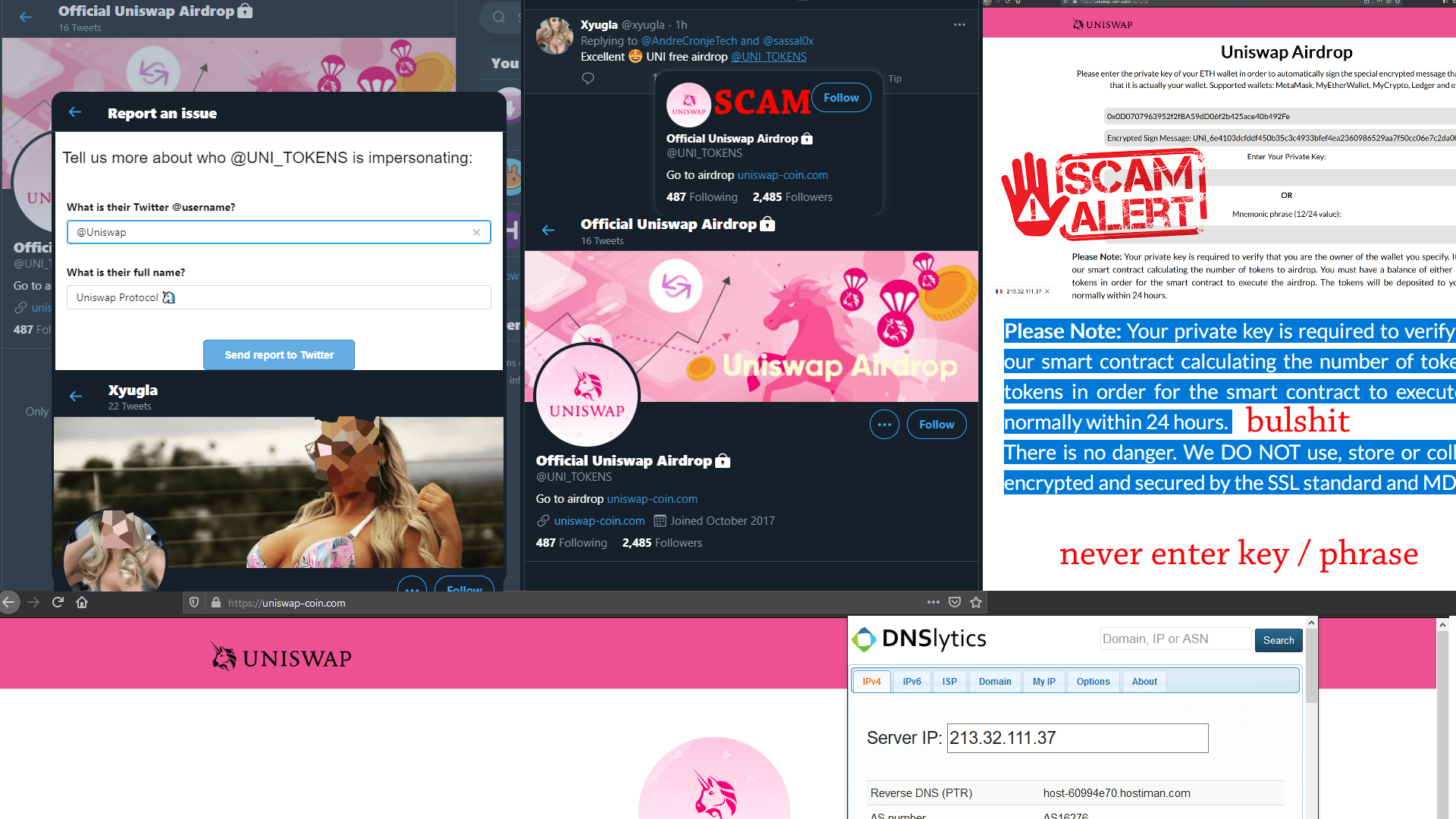
7. Fake uniswap airdrop, V3, sync, etc
Fake uniswap stealing seed:
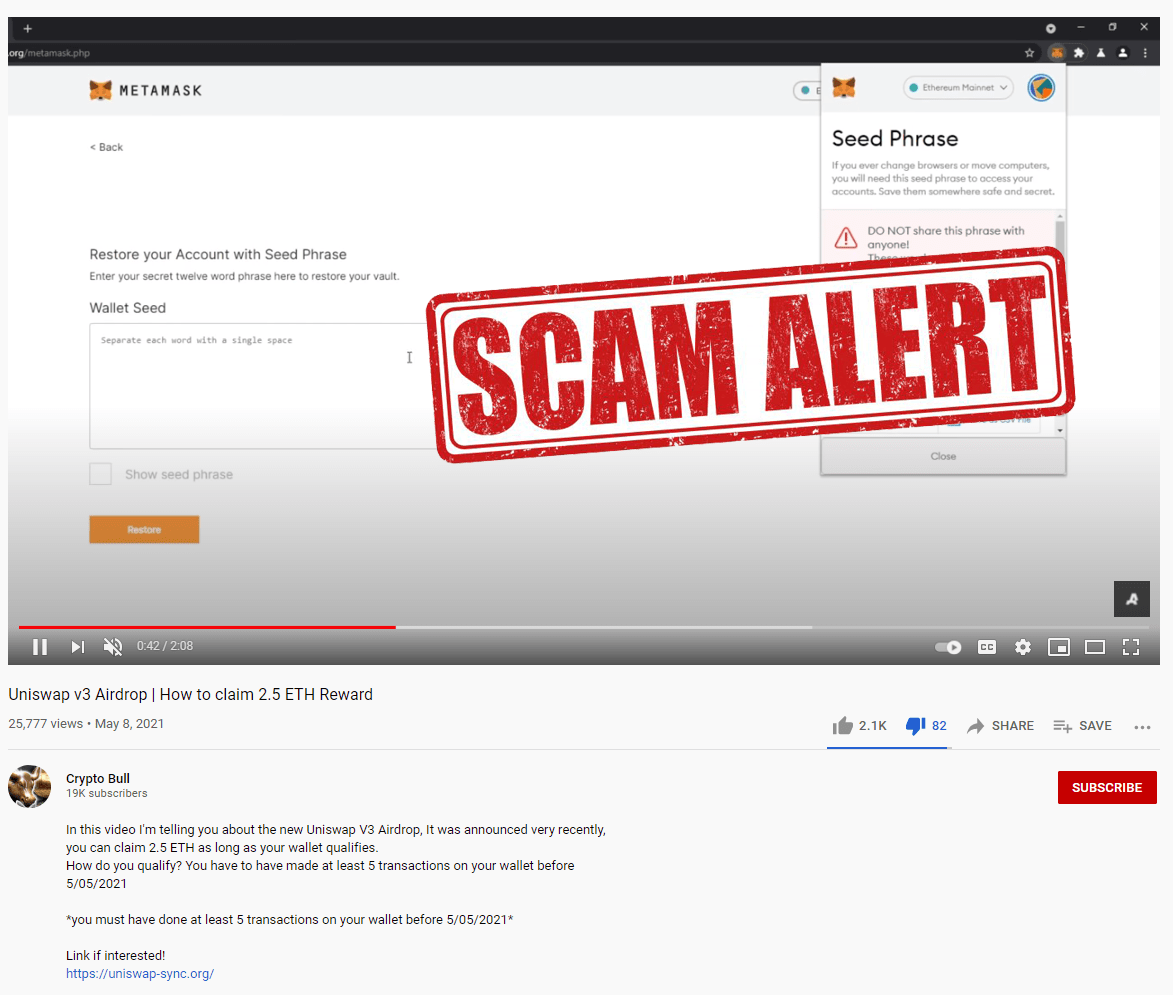
Fake Uniswap airdrop:
NEVER enter key or phrase! Especially in some dodgy site!
Uniswap clones about a node sync or version upgrade, scams.
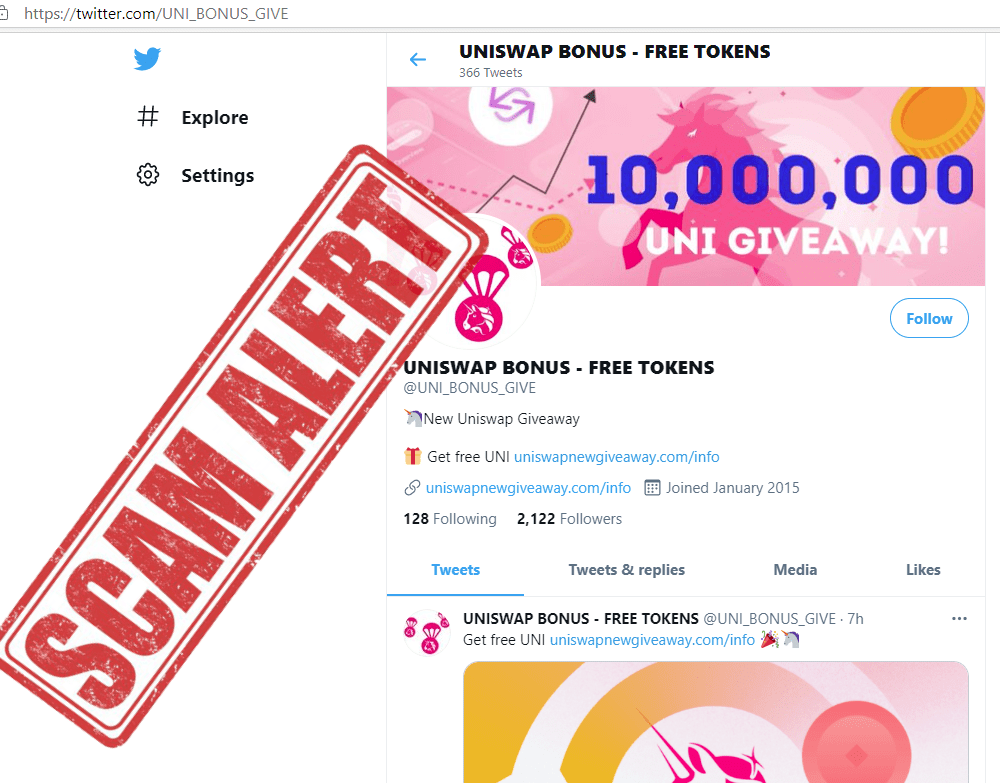
Fake airdrop twitter uniswap
Remember on DISCORD:
8. Compromised device
Never mine crypto and use a wallet on the same device.
Always use 2FA, best bet is to have a separate Chromebook or Macbook or PC/laptop that is not used for every day use, but only for crypto.
This can be a scary one. Copy and paste the “correct” wallet, but actually it gets replaced by malware to scammers wallet!
Or hacked PC and signed transaction actually signs TWO transactions, one hidden in the background! OUCH!
– Or modified background.js or metamask to approve hidden transaction EVEN WITH LEDGER.
Another example
– Fake Uniswap ICO site, with a dodgy .exe (teamviewer RAT hidden silent depoy)
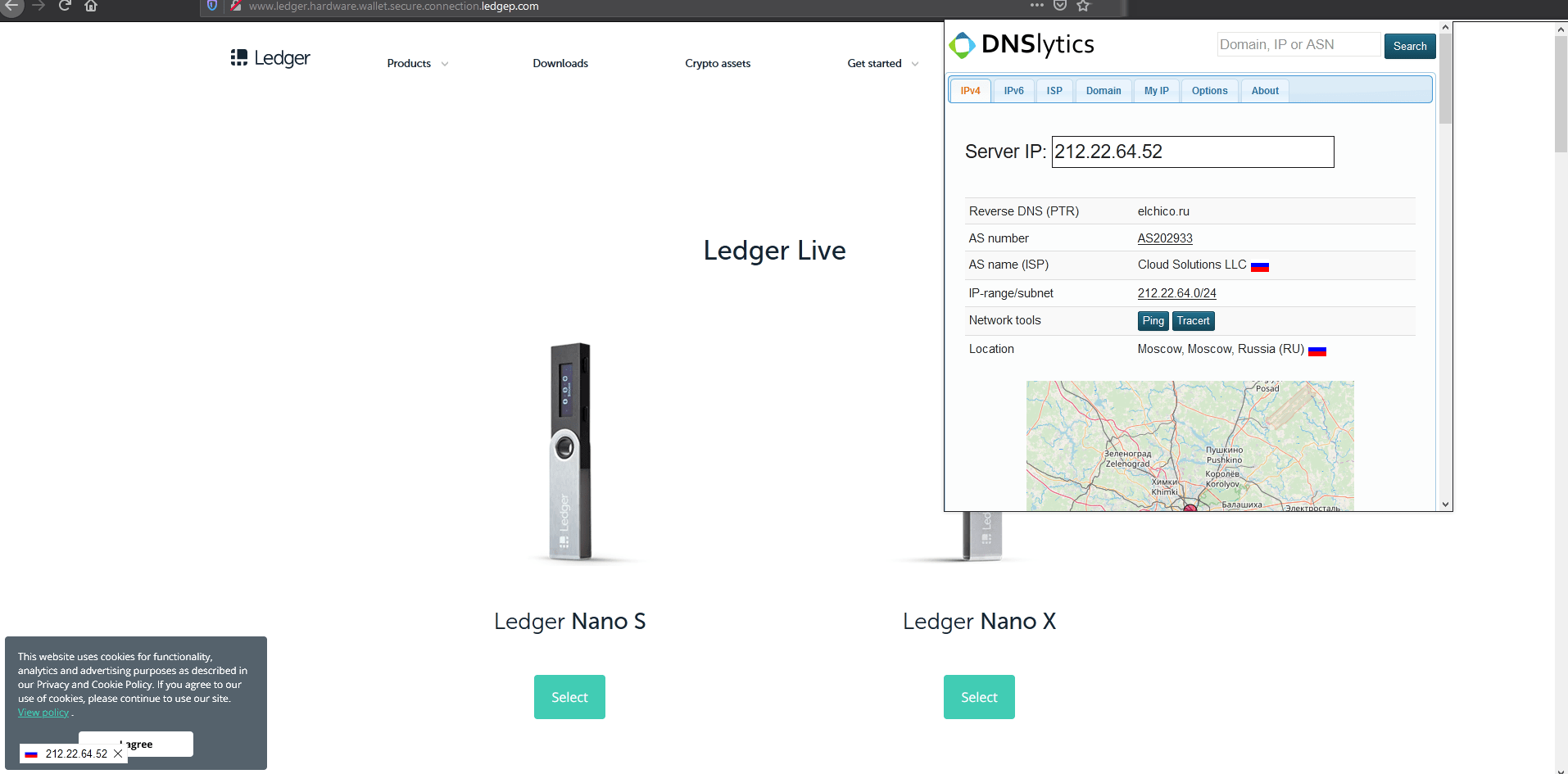
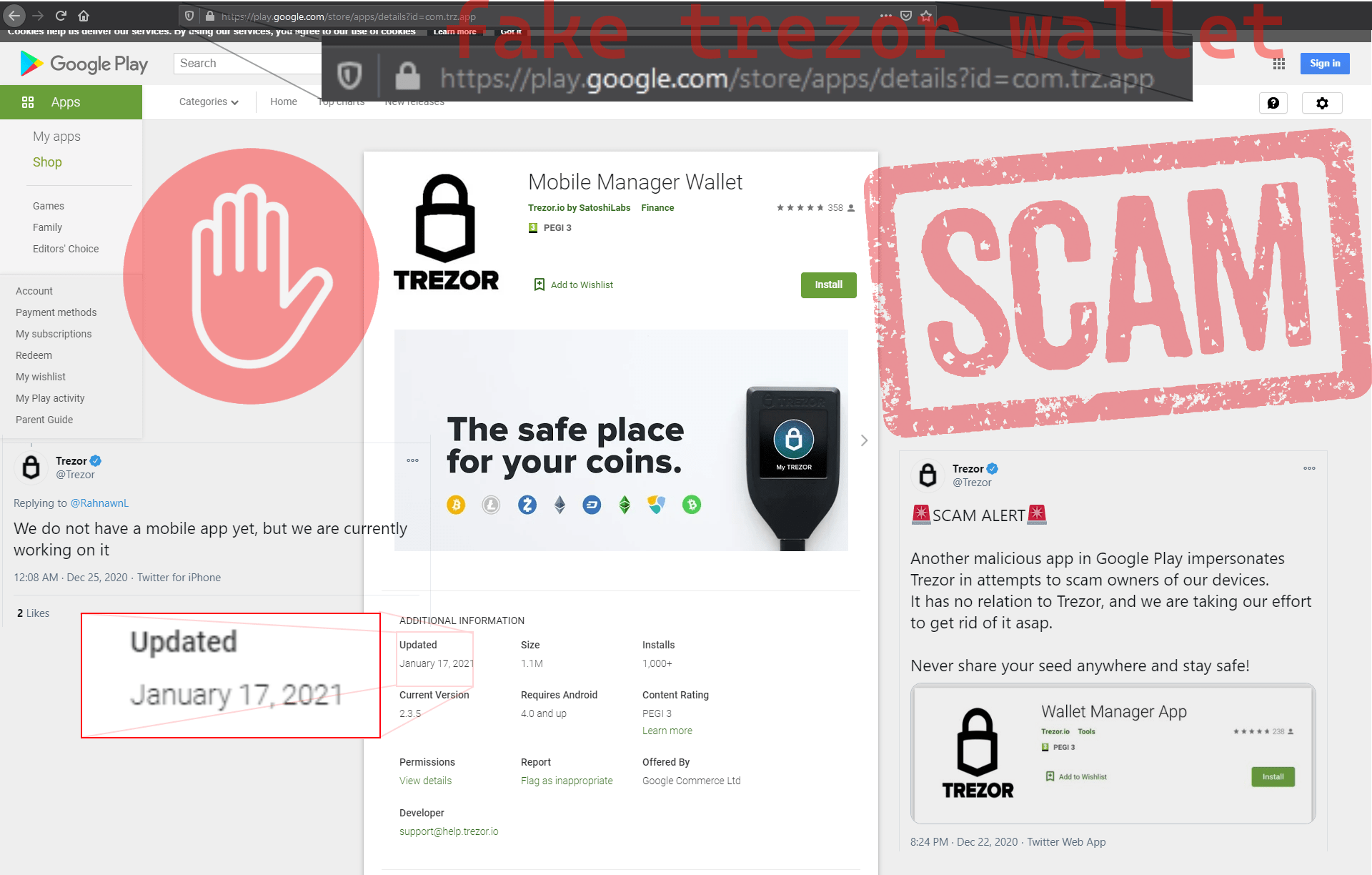
9. Fake Ledger and Trezor support
Ledger does not phone you. Nor do they want your backup phrase in a dodgy portal.
Fake ledger:
Fake Trezor:
10. Sim swapping
If you notice GSM service disruptions always assume sim hack!
Use authenticator app, not SMS!
⚠ Enable SINGLE DEVICE MODE to prevent 2FA app being cloned (AUTHY)!
11. Social engineering attacks and sextortion
Be careful who you chat with and who is asking you for your mothers maiden name or your first pet.
Make sure to scrub off metadata from photos before sharing.
(i.e. I have a video of you doing bad stuff, send BTC to avoid getting exposed)
If you got an email that somebody has a shameful video of you and extorts you, it is a scam.
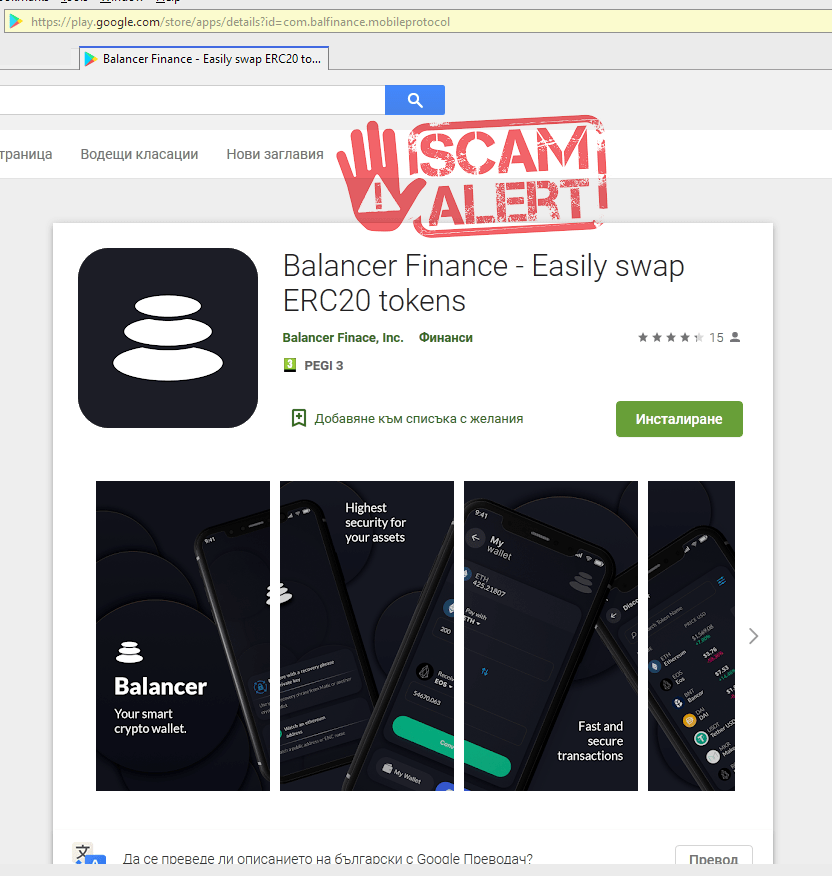
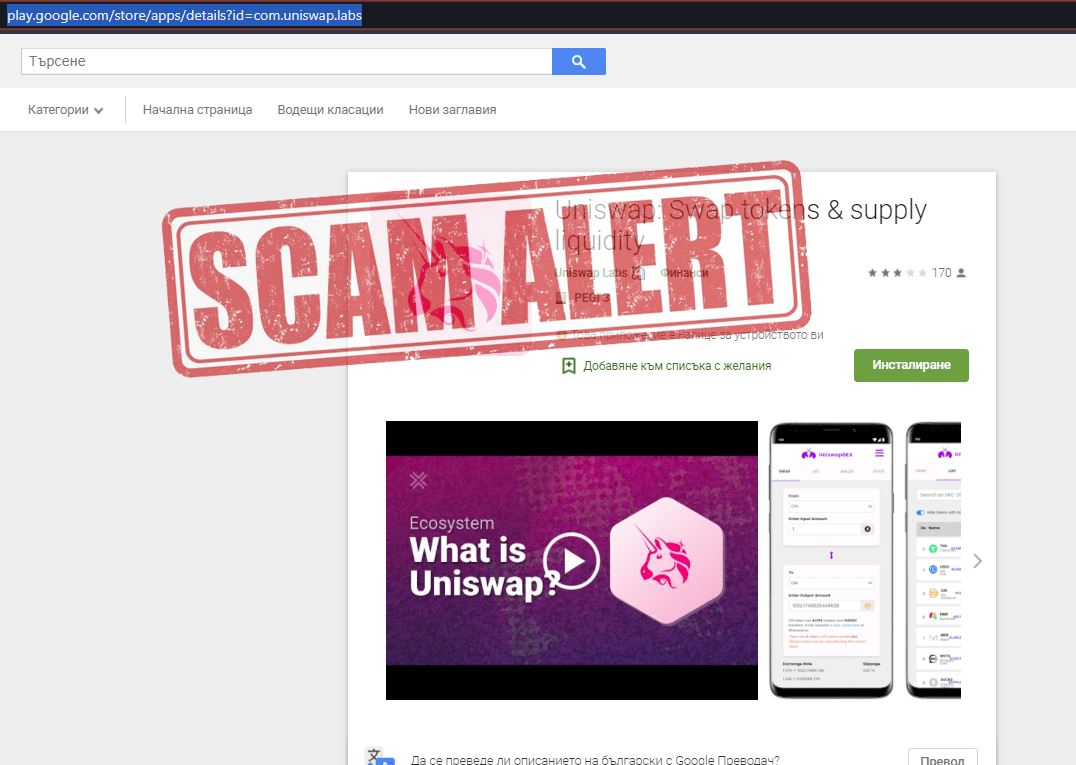
12. Fake wallets and google play store apps
For example TRON does not have an app yet, but hackers are uploading FAKE Tron apps to google play store, promising an airdrop.
Fake Polkadot
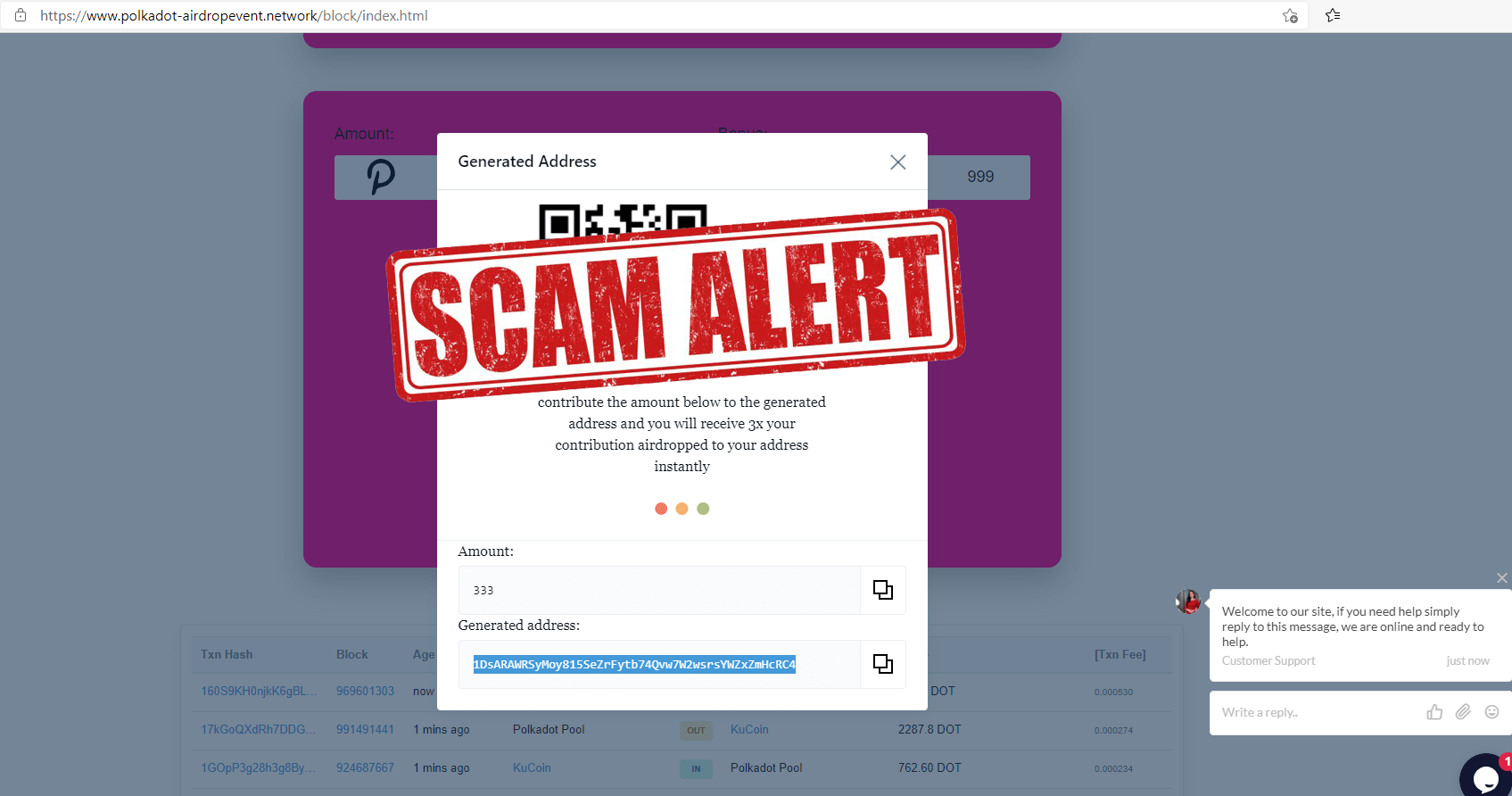
Fake Tron Airdrop

Fake Balancer app
Fake Google Play Uniswap app wallets
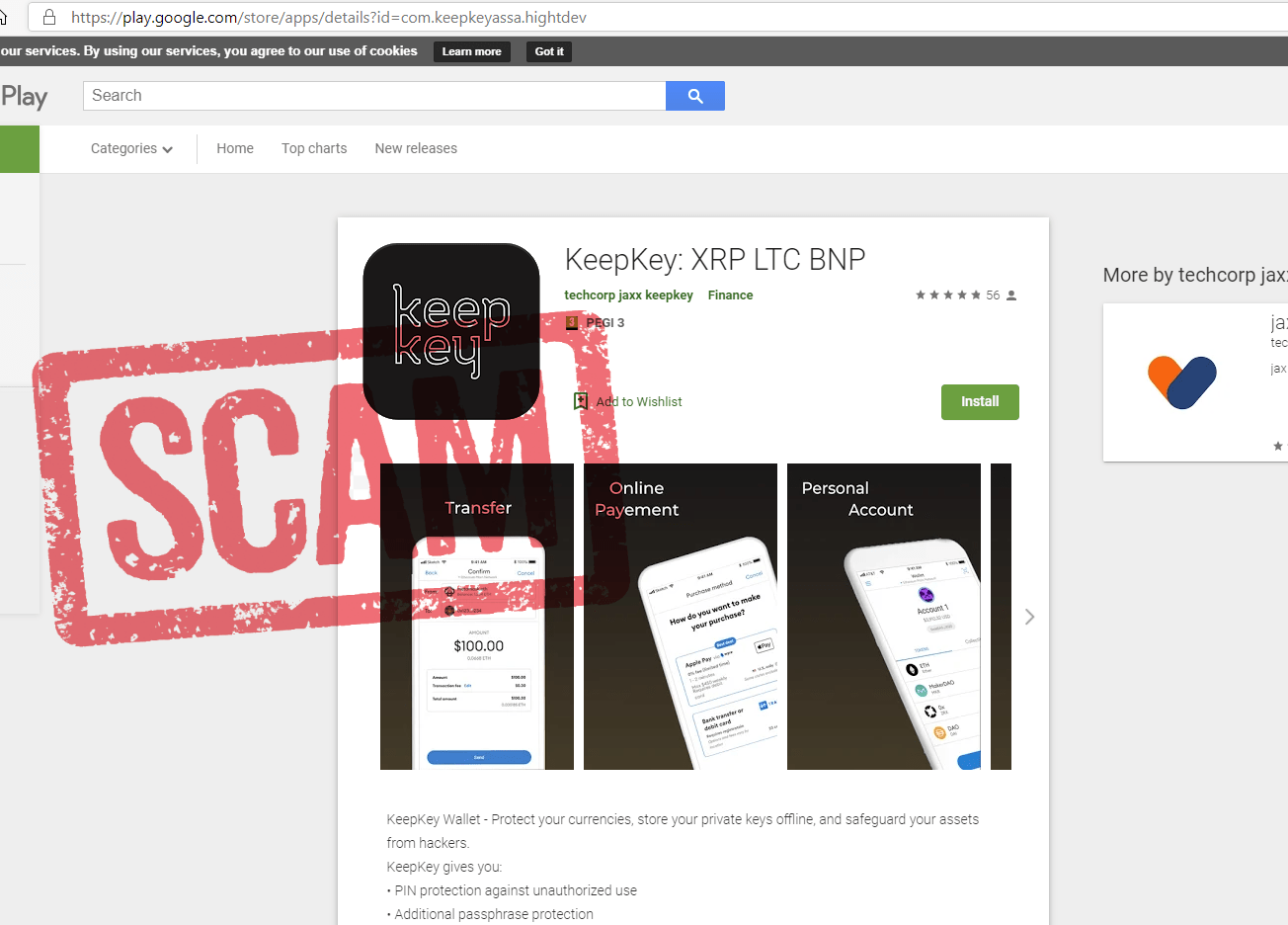
NEVER ENTER SEED OR KEYS!
Fake software updates
DON´T DOWNLOAD ANYTHING FRO LINKS YOU GOT IN DMS!
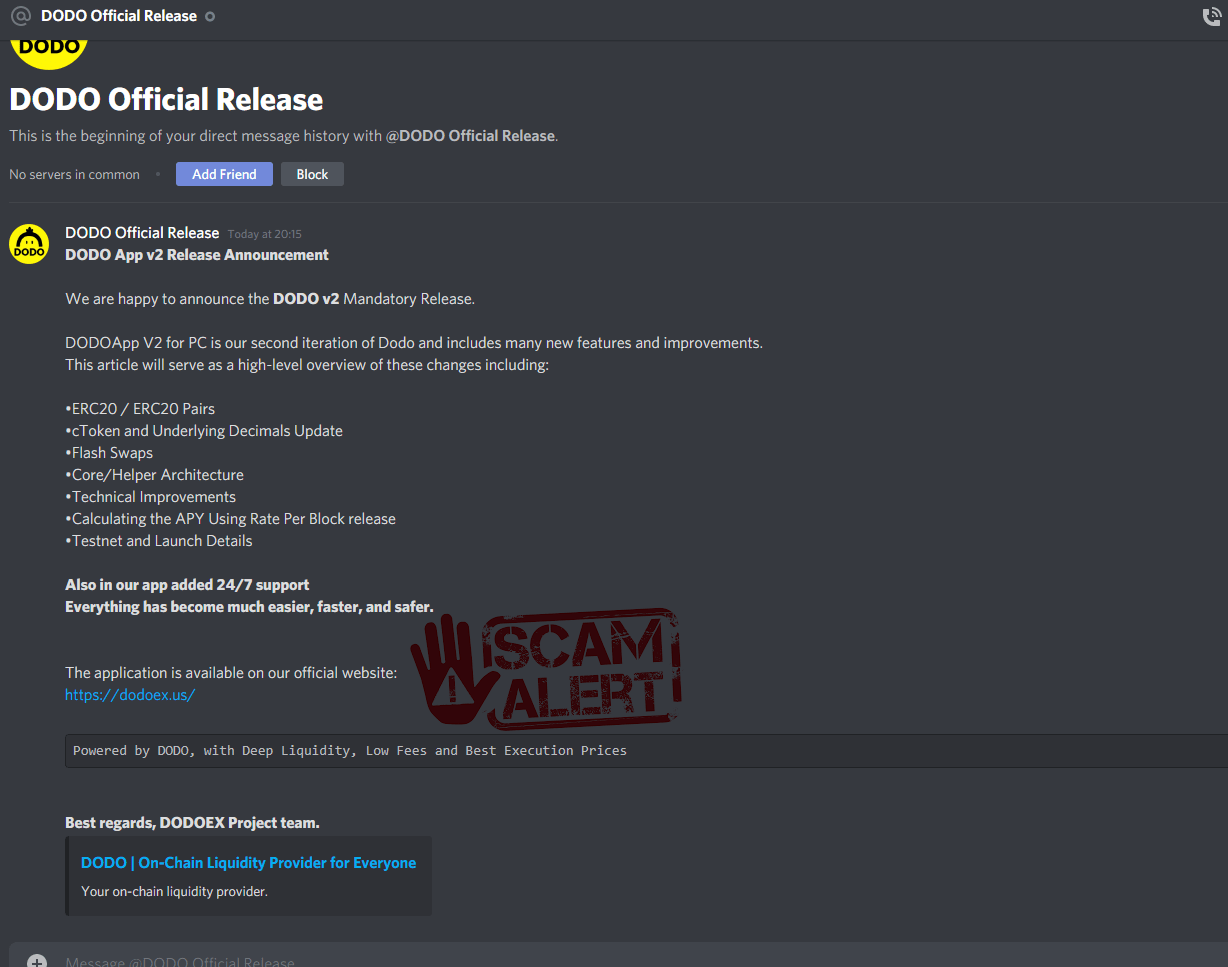
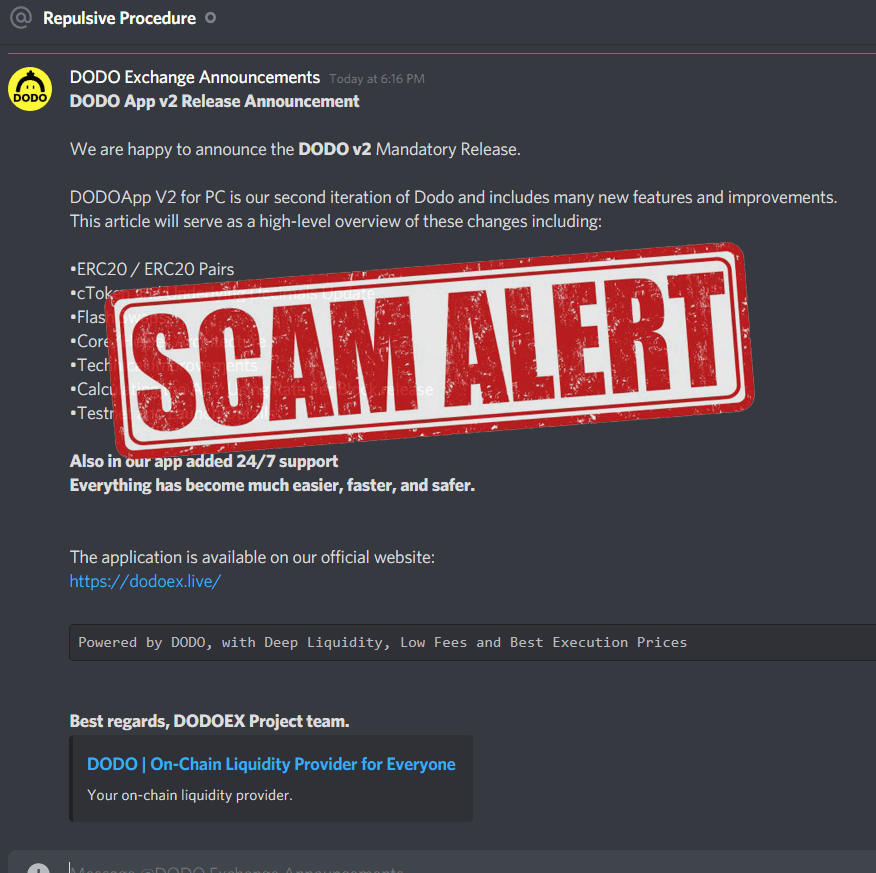
Fake Graph foundation “mandatory” update (Remcos RAT)
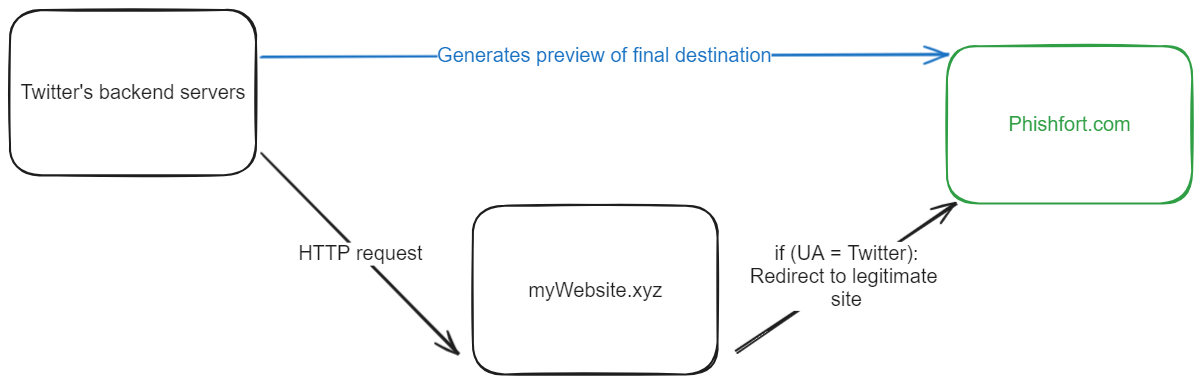
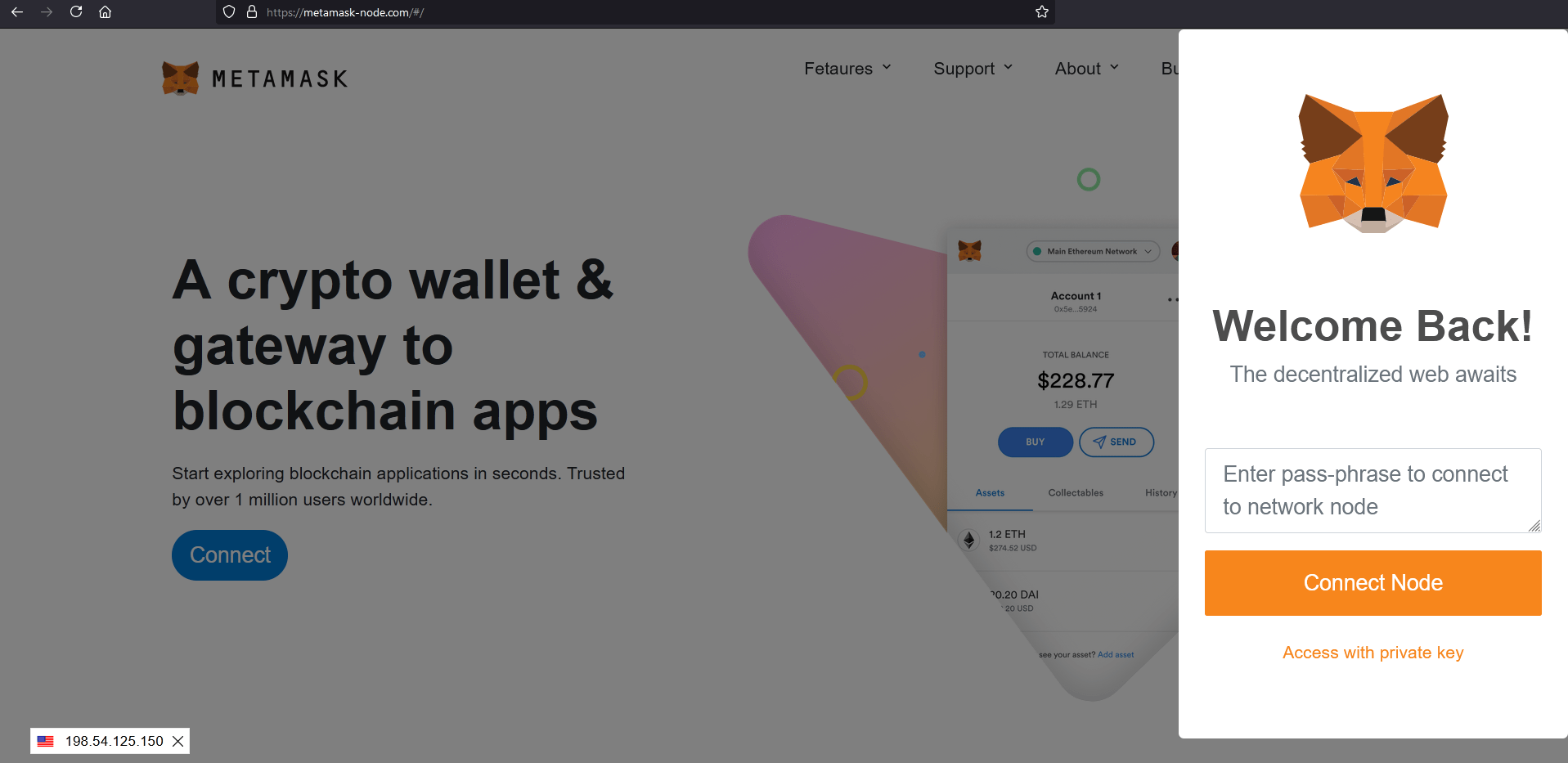
Fake Metamask
Metamask users are often invited to fake sites prompting them to enter seed phrase via various methods (email spam, scam DMs, twitter DMs, telegram and so on)
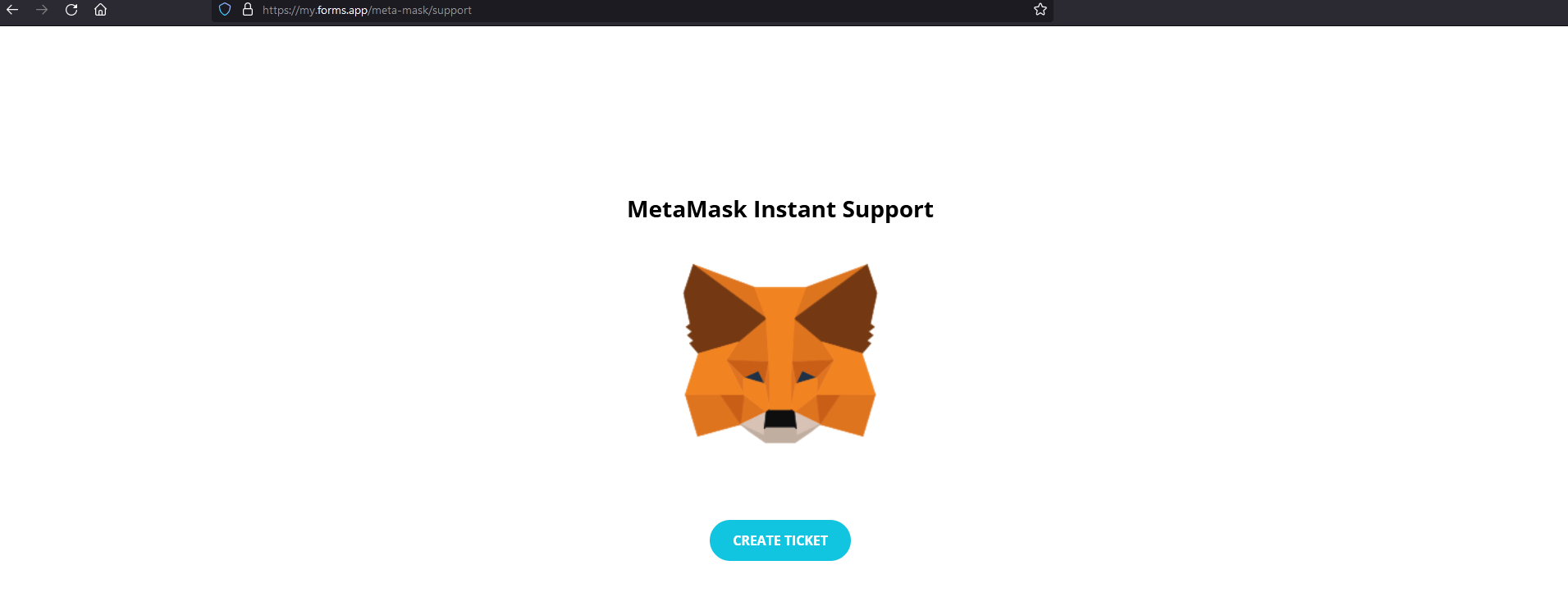
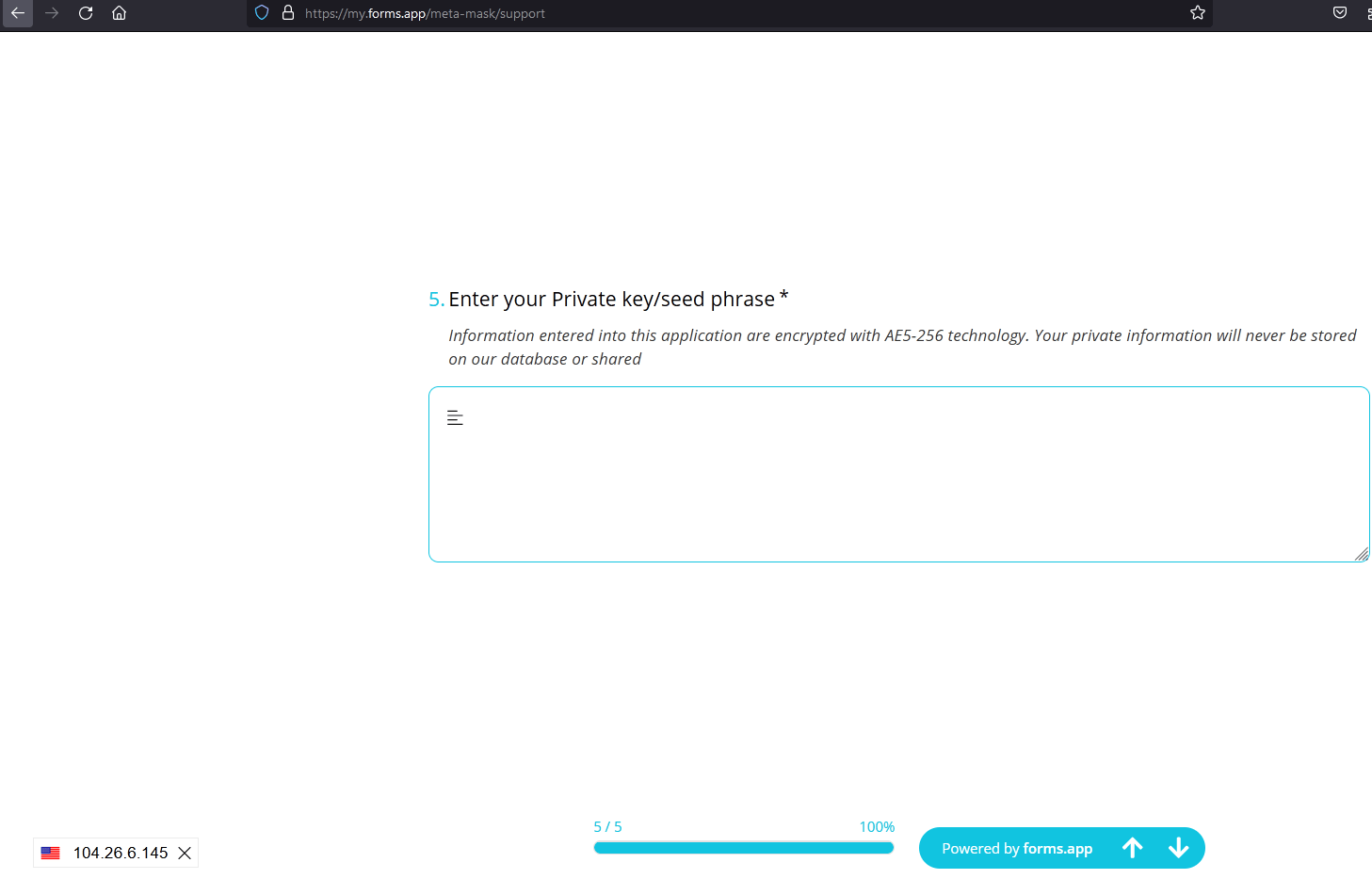
Another Metamask Scam:
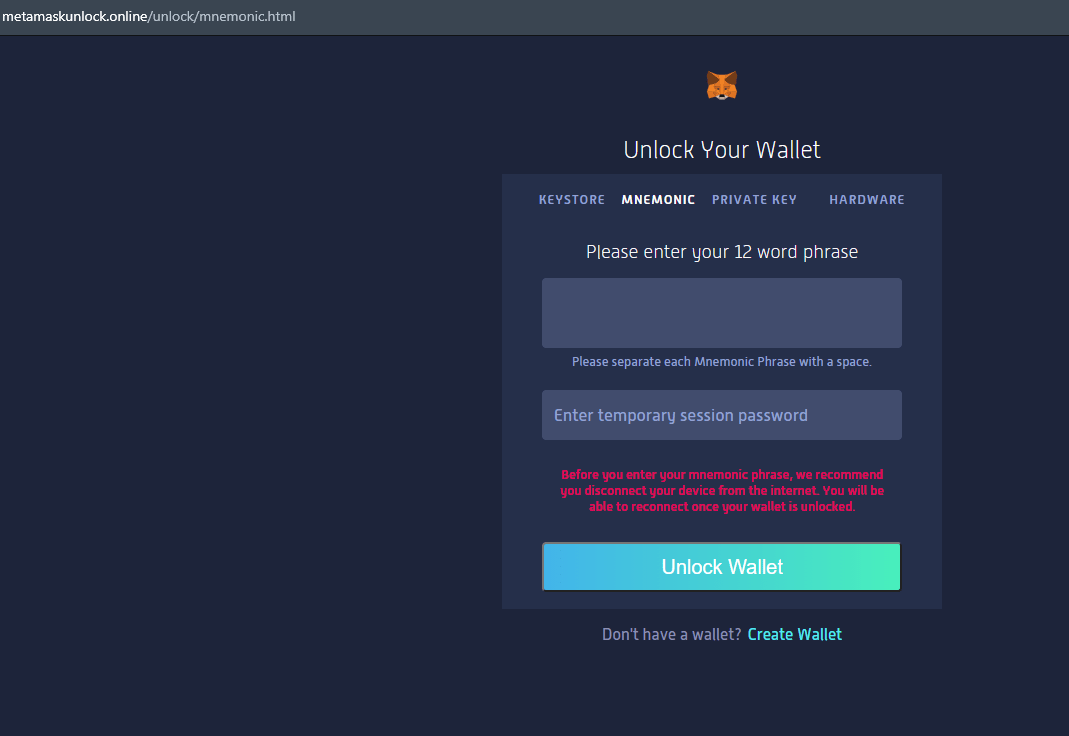
Another variation of a Metamask scam
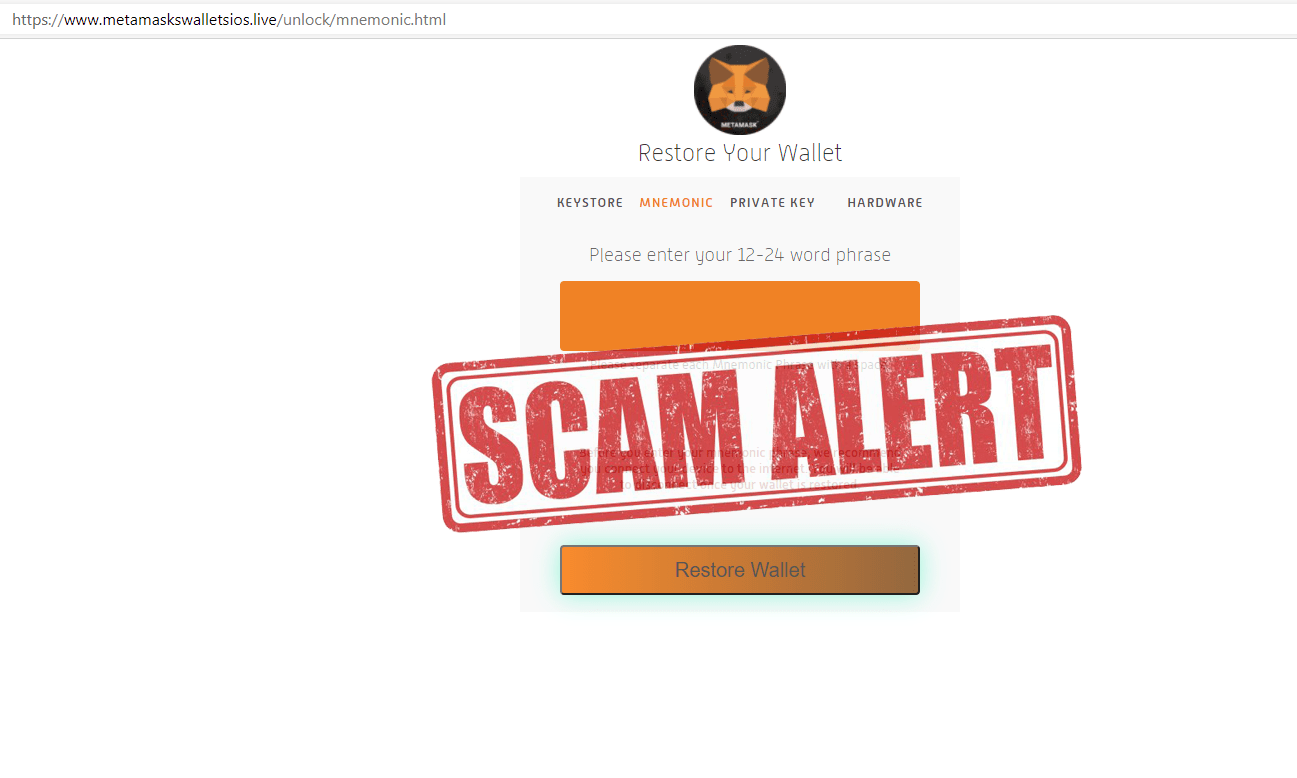
Another one
Ultimately, being aware of the different types of cryptocurrency scams will empower you to make better decisions and shield your assets.
It’s essential to share your knowledge about cryptocurrency scams to help others avoid falling prey to these malicious activities.
Protecting yourself from cryptocurrency scams involves staying informed and being cautious with your personal information.
Attack vectors such as domain squatting, executive impersonation, and SEO poisoning often go unnoticed by even vigilant internet users. PhishFort specializes in detecting and taking down phishing websites, mobile app clones, and fake social media content to protect your business and customers. By addressing these hidden but dangerous attack pathways, PhishFort ensures comprehensive brand protection from lesser known but potent cyber threats. Learn about phishing tactics targeting browser extensions in Chrome Extension Phishing and dive into phishing techniques in crypto with Phishing Enumeration | Understanding a Crypto Phishing Attack.
Final Thoughts
Cryptocurrency scams are evolving – from hacked YouTube streams to complex smart contract exploits. The best defense is awareness and proactive phishing protection.
Engaging in online discussions about cryptocurrency scams can help raise awareness and educate others.
Stay safe and vigilant against cryptocurrency scams by continually educating yourself and sharing your knowledge with others.
PhishFort’s real-time threat intelligence helps identify, investigate, and remove phishing websites, fake investment platforms, and fraudulent social media accounts targeting crypto users and brands.
Working together as a community to combat cryptocurrency scams can significantly reduce the number of victims.
Stay informed and protected. Learn more in:
Test our Brand Protection Services
With PhishFort’s hands-free, fully managed service, you can trust us to safeguard your brand without delay, allowing you to focus on what matters most. Test our Brand Protection Services today and secure peace of mind with rapid, reliable protection from PhishFort.