Digital threat protection has become a core requirement for organizations operating in an environment where attacks no longer target only internal systems, but entire digital ecosystems.
From phishing campaigns and impersonation to fraudulent websites and malicious domains, modern threats exploit the public internet to reach users, customers, and employees at scale. Digital threat protection focuses on identifying, monitoring, and disrupting these threats before they cause damage.
What Is Digital Threat Protection?
Digital threat protection refers to a set of capabilities designed to detect and mitigate malicious activity targeting an organization’s digital presence.
This includes threats such as:
Phishing and scam websites
Brand and domain impersonation
Executive and employee impersonation
Fake social media profiles and ads
Fraudulent web infrastructure
Unlike traditional security controls that operate inside the network, digital threat protection addresses external, internet-facing threats that exist beyond the organization’s perimeter.
Why Digital Threats Are Increasing
Attackers increasingly rely on digital channels because they offer:
Low cost and fast setup
Global reach
Short-lived infrastructure that evades detection
High return through fraud, credential theft, and brand abuse
As a result, many digital threats are discovered only after users or customers have already been affected.
Common Digital Threat Protection Use Cases
Phishing and Online Fraud
Threat actors deploy convincing phishing pages that mimic login portals, payment flows, or customer services. Digital threat protection enables early detection and rapid takedown of these assets.
Brand and Domain Abuse
Lookalike domains and fake websites exploit brand trust. Monitoring domain registrations and online content helps identify abuse before campaigns scale.
Executive and Employee Impersonation
Impersonation across email, web, and social platforms is commonly used to support fraud and social engineering. Digital threat protection helps detect impersonation attempts targeting leadership and internal teams.
Customer Trust and Reputation Protection
When customers encounter scams or fraudulent pages using a brand’s identity, trust erodes quickly. Digital threat protection reduces exposure and reputational impact.
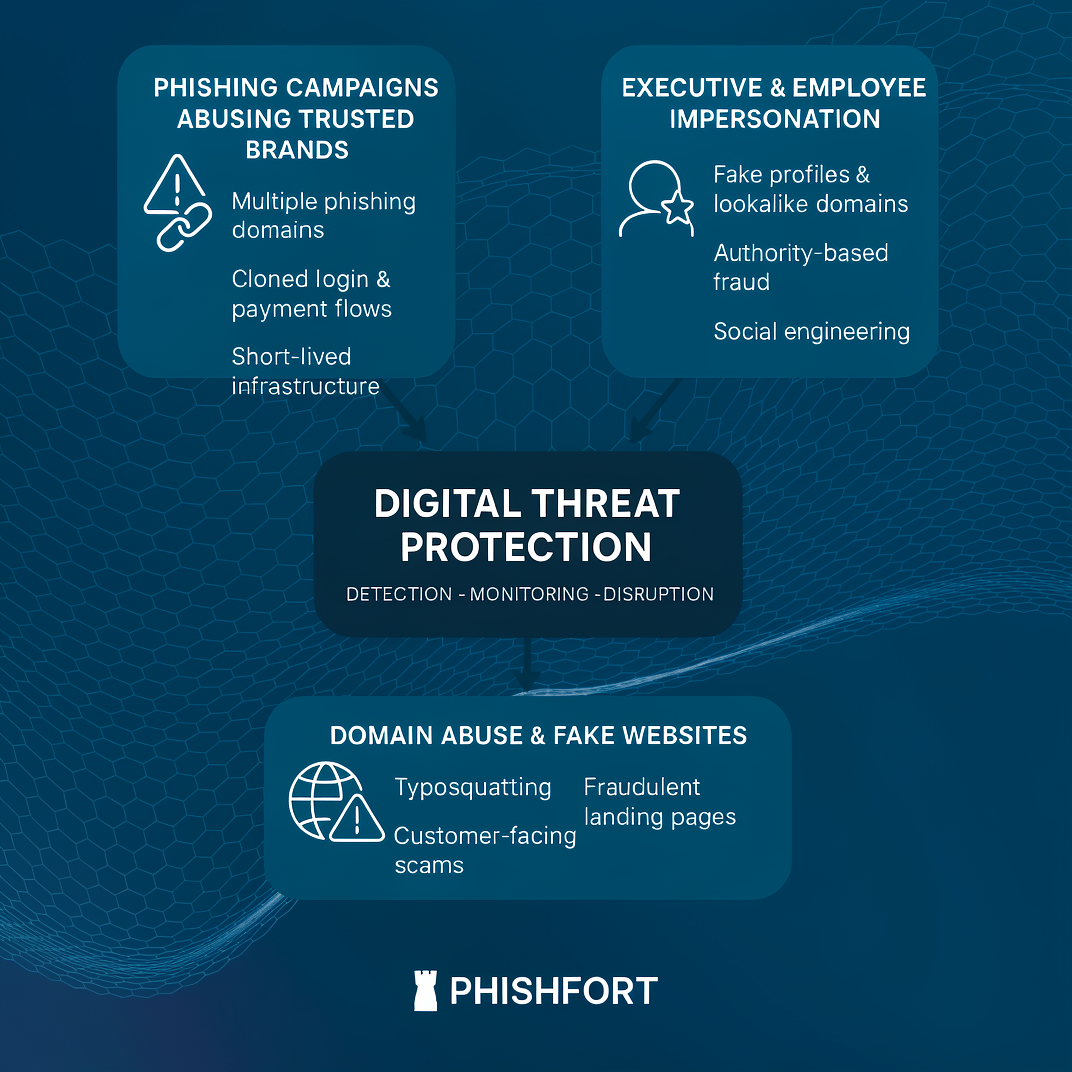
How Digital Threat Protection Works
An effective digital threat protection strategy typically combines:
Continuous monitoring of domains, web content, and online platforms
Automated detection of malicious indicators and patterns
Context-aware analysis to reduce false positives
Rapid response workflows to disrupt or remove threats
Detection alone is not enough. The value lies in how quickly threats can be validated and neutralized.
Detection, Monitoring, and Disruption at Scale
Digital threats move fast. Campaigns may last hours or days, not weeks.
Digital threat protection enables organizations to:
Detect threats early
Prioritize based on risk and exposure
Act quickly to disrupt malicious infrastructure
This reduces operational overhead while limiting the window of opportunity for attackers.
Digital Threat Protection as a Business Requirement
Digital threats impact more than security teams. They affect:
Brand reputation
Customer confidence
Financial performance
Legal and compliance exposure
Treating digital threat protection as a reactive or ad-hoc effort leaves organizations vulnerable. Continuous protection is now a baseline requirement for digital operations.
Real-World Scenarios and How Organizations Disrupt Modern Attacks
Digital threat protection is no longer a theoretical capability. In practice, it is defined by how quickly organizations can detect and disrupt real attacks operating on the open internet.
Today’s most damaging threats rarely involve breaching internal systems. Instead, attackers exploit trust, visibility gaps, and speed by abusing brands, identities, and digital infrastructure outside the traditional security perimeter.
Below are common real-world scenarios where digital threat protection becomes critical.
Case 1: Phishing Campaigns Abusing Trusted Brands
In many attacks, threat actors deploy phishing campaigns that closely replicate legitimate brand experiences.
These campaigns often involve:
Multiple phishing domains launched in parallel
Cloned login or payment flows
Infrastructure designed to stay live only for hours or days
Because these sites look legitimate and contain no malware, traditional security tools frequently miss them.
Why this matters: Users and customers are compromised outside the organization’s environment, but the reputational and financial impact falls on the brand.
How digital threat protection helps
Early detection of newly registered malicious domains
Correlation of related phishing assets into campaigns
Rapid disruption before the campaign reaches scale
According to the FBI’s Internet Crime Complaint Center (IC3), phishing and digital fraud remain among the most financially damaging cybercrime categories worldwide.
Case 2: Executive and Employee Impersonation Enabling Fraud
Another frequent scenario involves impersonation of executives or employees to support fraud and social engineering.
Attackers may:
Create fake executive profiles
Register lookalike domains
Combine web assets with email or messaging outreach
The success of these attacks relies on authority and urgency rather than technical exploits.
Why this matters: Even a single convincing impersonation can trigger financial loss, internal confusion, or partner distrust.
How digital threat protection helps
Monitoring of executive and employee identities across digital channels
Detection of impersonation signals tied to web infrastructure
Coordinated response to remove fake assets quickly
This type of impersonation rarely happens in isolation. It is often part of broader digital campaigns that require continuous visibility to stop.
Case 3: Domain Abuse and Fake Websites Targeting Customers
Domain abuse remains one of the most persistent digital threats.
Common patterns include:
Typosquatted domains
Fake customer support or promotional websites
Fraudulent landing pages promoted via ads or search
Customers often encounter these assets before the organization becomes aware of them.
Why this matters: From the customer’s perspective, the distinction between a fake site and the real brand is irrelevant. Trust erodes either way.
How digital threat protection helps
Continuous monitoring of domain registrations and web content
Risk-based validation of suspicious assets
Fast takedown workflows to limit exposure
European cybersecurity agencies such as ENISA consistently highlight phishing, impersonation, and domain abuse as persistent digital threats across industries.
What These Scenarios Have in Common
Across these cases, the challenge is not the lack of security controls. It is time.
Attackers rely on:
Speed of infrastructure creation
Short-lived campaigns
Operating entirely outside internal environments
Digital threat protection reduces the time attackers have to exploit trust and scale their campaigns.
Why Digital Threat Protection Is a Business Requirement
These threats affect more than security teams. They impact:
Brand reputation
Customer confidence
Revenue and operational continuity
Legal and compliance exposure
Treating digital threat protection as a reactive task means accepting unnecessary risk.
Final Thoughts
Digital threat protection is not about predicting every attack. It is about detecting malicious activity early and disrupting it fast enough to limit real-world impact.
Organizations that combine continuous monitoring, accurate detection, and rapid disruption are better positioned to protect their brands, users, and digital ecosystems against modern threats. Learn how digital threat protection enables faster detection and disruption of threats operating on the open internet.



