Takedowns are part of the internet’s plumbing. People want harmful or unauthorized content removed, but the path from discovery to removal is rarely linear. Victims see a binary outcome – either the content is gone or it isn’t. Practitioners know the road is full of grey: overlapping jurisdictions, shifting policies, and technical edge cases. The “right” path depends on the type of abuse and the entities involved.
Who Actually Handles a Domain Takedown
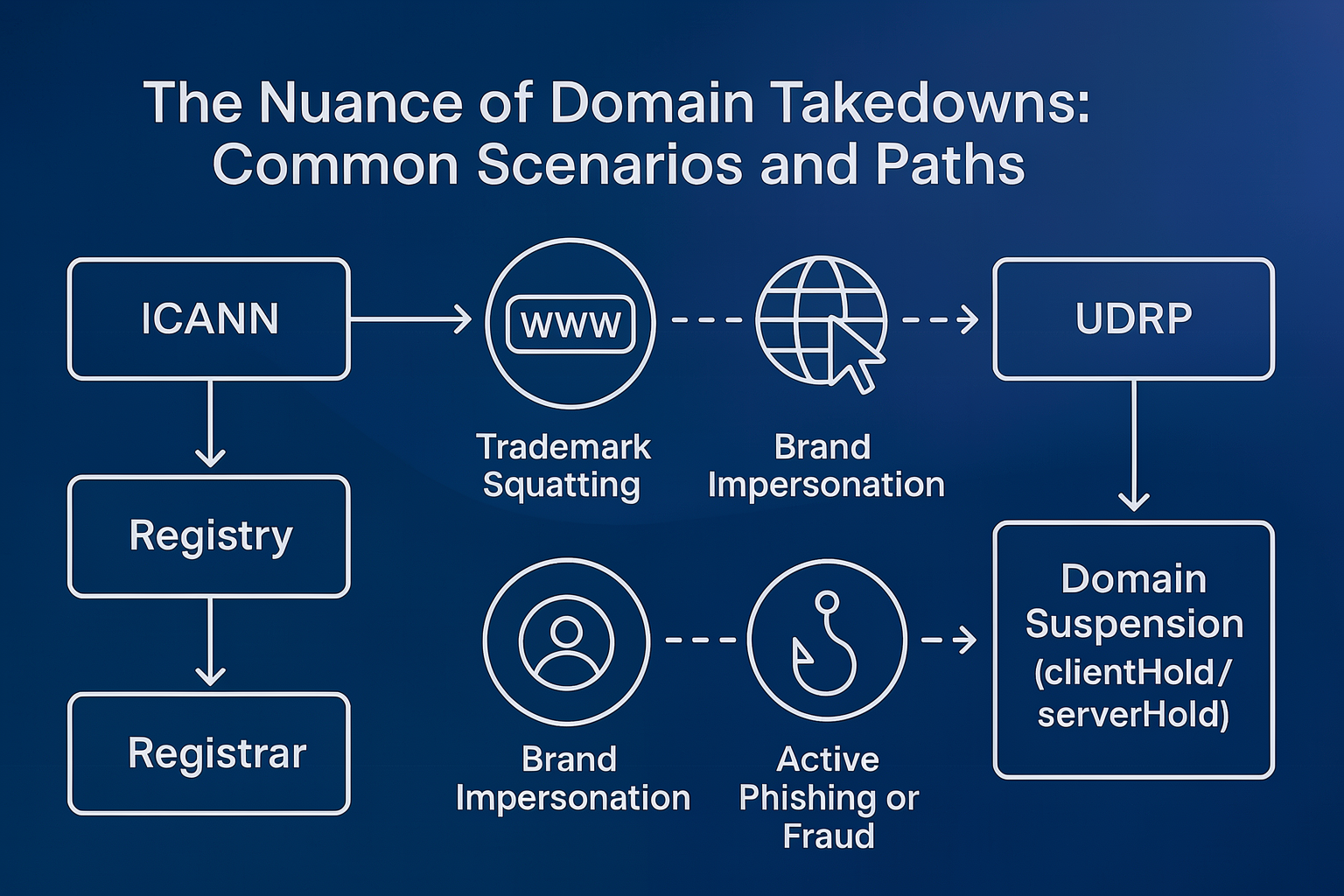
Most domain takedown requests revolve around a domain name – the text string that points users to the offending content. Behind every domain sits a small ecosystem:
ICANN: The nonprofit steward of the domain name system that sets baseline policy for most generic top-level domains (gTLDs).
The registry: The operator of a top-level domain (TLD), such as Verisign for .com or a national authority like CIRA for .ca.
The registrar: The storefront where the domain was registered – e.g., GoDaddy, Namecheap, or Squarespace.
For most gTLDs (.com, .org, etc.), these parties operate under ICANN contracts that require mechanisms to mitigate DNS abuse and to handle trademark disputes via the Uniform Domain Name Dispute Resolution Policy (UDRP).
Why Outcomes Vary (and Where UDRP Fits)
Three factors complicate domain takedowns:
Policy interpretation: ICANN, registries, and registrars often read obligations differently, producing inconsistent decisions.
Jurisdiction: Country-code TLDs (ccTLDs like .de or .jp) aren’t bound by ICANN contracts. They follow national policy, which may offer limited recourse.
UDRP limits: UDRP can be costly and slow, and it requires proof the domain was registered and used in bad faith – e.g., intent to confuse users, resell the domain, or obstruct the trademark holder. Depending on the evidence, that bar can be high.
The net: there’s a framework, but consistent outcomes aren’t guaranteed – especially with ccTLDs.
The Goal: Domain Suspension (clientHold/serverHold)
When the goal is a full domain suspension, you’re typically aiming for:
clientHold: A registrar-applied status that removes the domain from the DNS.
serverHold: A registry-applied status with the same effect, often perceived as more definitive.
Common Takedown Scenarios and Escalation Paths
The best strategy depends on what the domain is doing. Below are three trademark-related scenarios, each with different levers.
Scenario 1: Trademark Squatting (No Content Yet)
An unknown registrant buys a domain with your trademark. There’s no website or email – just a registration that could be used later for phishing or fraud.
How registrars/registries see it: Without evidence of active abuse, they typically won’t act. They view this as a potential trademark dispute, not DNS abuse, and won’t adjudicate on content or intent.
Your options
Try to purchase the domain: Effective if you need certainty, but costly at scale and can validate squatting behavior.
Monitor proactively for abuse: Use threat monitoring (e.g., a phishing detection service) to catch any shift to malicious use, then report swiftly for takedown.
File a UDRP: Possible, but success is unlikely without strong bad-faith evidence. If the domain never hosts content or email, proving intent is hard – especially for smaller brands.
Trade-off: Weigh risk, cost, and likelihood of misuse. For high-risk brands, monitoring paired with fast reporting is often the pragmatic path.
Scenario 2: Brand Impersonation (Look-Alike Site, No Data Capture)
The domain hosts a copy of your site or store but doesn’t appear to collect credentials, payment details, or PII.
How registrars/registries see it: You now have clearer bad-faith indicators, but many providers still classify this as a “content issue” rather than DNS abuse. They generally avoid adjudicating content.
Your options
File a UDRP: Your odds improve with evidence of impersonation and confusion.
Investigate for hidden collection: Look for forms, scripts, or redirects capturing PII. If found, it becomes clear DNS abuse (see Scenario 3).
Warn customers: Publish a notice, update support scripts, and flag the look-alike domain in user communications.
Scenario 3: Active Phishing or Fraud
The domain infringes your mark and actively steals credentials, PII, or payment info.
How registrars/registries see it: This crosses from “content” into DNS abuse. Provide concrete evidence – timestamps, screenshots, screen recordings, HTTP captures – and you’ll usually see a swift suspension (clientHold or serverHold).
What to do next: Keep monitoring. Bad actors sometimes remove content temporarily to argue for reinstatement, then relaunch.
Beyond Trademark Abuse: Other Takedown Routes
Copyright Infringement (DMCA)
If a site uses your copyrighted work (text, images, software) but the domain name itself isn’t the issue, a DMCA takedown to the hosting provider is often the fastest remedy. It removes the content, not the domain, but can be highly effective in jurisdictions that recognize the DMCA.
Phishing Without Trademark Infringement
Scammers often use generic domains like account-services-login.com or secure-payment-portal.net. Trademark questions are irrelevant here; the harm is in how the domain is used. Report directly to the registrar/registry as DNS abuse, as in Scenario 3.
Conclusion: Match Strategy to Harm
There’s no single playbook for domain takedowns. The key is to identify the harm and choose the right channel:
Trademark conflict? Consider the UDRP process and parallel brand-protection actions.
Content misuse? Target the hosting provider through a DMCA notice.
Clear DNS abuse like phishing or fraud? Report directly to the registrar and registry for domain suspension.
By matching your takedown strategy to the specific behavior and working with the right entities, you can navigate the nuances more effectively – and protect your brand online.
If you’re facing phishing attacks, impersonation, or other forms of domain abuse, PhishFort can help you detect, report, and accelerate the takedown process. Our team specializes in identifying malicious domains and coordinating with registrars and registries to ensure fast, lasting removal.
FAQs
What’s the fastest way to stop an active phishing site?
Report to the registrar and registry with concrete evidence (screenshots, network captures). Ask for domain suspension (clientHold/serverHold) and alert the hosting provider to remove the content.
When should I choose UDRP over a DMCA?
Use UDRP for trademark disputes around the domain name itself. Use DMCA when copyrighted material is being used on the site, regardless of the domain string.
Do ccTLDs follow ICANN rules?
Not necessarily. ccTLDs follow national policy, which can change your options and timelines. Look up that ccTLD’s specific abuse process.
Can buying the domain from a squatter backfire?
It can be effective for high-risk terms, but it’s expensive at scale and can incentivize more squatting. Pair strategic purchases with monitoring and rapid takedown workflows.
What evidence should I include in an abuse report?
Date/time, full URLs, screenshots or video, HTTP headers/responses, and any indicators of credential or payment capture. The clearer the evidence, the faster the action.