Why Cyber Attackers Commonly Use Social Engineering Attacks on Social Media
The rise of social media has transformed communication – but it has also created new attack vectors for cybercriminals. Today, attackers exploit social platforms not only to impersonate brands but also to manipulate users psychologically. Understanding what is the goal of most social media based attacks and why cyber attackers commonly use social engineering attacks is key to building effective defenses for your business and customers.
What Is the Goal of Most Social Media-Based Attacks?
The primary goal of most social media-based attacks is to gain trust and leverage it for malicious purposes. Attackers exploit the social nature of these platforms to achieve objectives such as:
Stealing login credentials through fake login pages or phishing messages.
Impersonating brands or executives to deceive customers or employees.
Spreading malware via malicious links disguised as promotions or updates.
Harvesting sensitive data from messages or account takeovers.
Damaging brand reputation by publishing fake or misleading content.
Unlike traditional phishing, social media attacks exploit emotional and behavioral cues. Users trust familiar accounts, engage quickly, and often overlook red flags. This trust is exactly what cyber attackers aim to exploit.
Why Do Cyber Attackers Commonly Use Social Engineering Attacks?
To understand why cyber attackers commonly use social engineering attacks, we must look at how human psychology drives these schemes. Attackers know that it’s often easier to trick a person than to hack a system.
1. People Trust Familiar Platforms
Users spend hours daily on social networks like Facebook, Twitter, and LinkedIn. The sense of familiarity lowers skepticism, making users more likely to click suspicious links or respond to fake messages.
2. Emotional Manipulation Works
Social engineering preys on emotion – urgency, fear, excitement, or curiosity. A message saying “Your account has been locked – verify now” can push even cautious users to act without thinking.
3. Massive Reach and Low Cost
Launching a phishing campaign on social media requires minimal resources but offers access to millions of potential victims. Automation tools and fake profiles make it easy for attackers to scale these operations globally.
4. Brand and Executive Impersonation
Attackers create fake corporate or executive profiles that look nearly identical to legitimate ones. Victims often believe they are communicating with real representatives, which makes deception effortless.
5. Weak Account Security
Many users reuse passwords or fail to enable two-factor authentication. Once an attacker gains access to one account, they can often infiltrate several others through password reuse.
6. Easy Data Collection
Public profiles contain valuable data – emails, job titles, interests – that attackers can use to craft believable phishing messages. The abundance of open information fuels targeted, realistic attacks.
7. Low Detection and Fast Impact
Social media’s real-time nature means scams can spread rapidly before detection systems react. Attackers exploit trending topics and hashtags to appear legitimate and maximize visibility.
Real-World Example: The BP Incident
In 2010, after the BP oil spill disaster, a fake Twitter account called @BPGlobalPR gained more followers than BP’s official page. While it began as satire, it demonstrated how quickly brand impersonation can spread – and how little effort it takes for attackers to damage reputation.
This illustrates what is the goal of most social media based attacks: to control a brand narrative, exploit public trust, and amplify chaos.
How Businesses Can Defend Against Social Engineering Attacks
Fighting social engineering on social media requires more than awareness – it demands continuous monitoring, rapid response, and the right tools.
Monitor for brand impersonation on all platforms.
Train employees to recognize phishing and suspicious messages.
Implement two-factor authentication (2FA) for all social media accounts.
Use threat detection technology to flag fake profiles and malicious content.
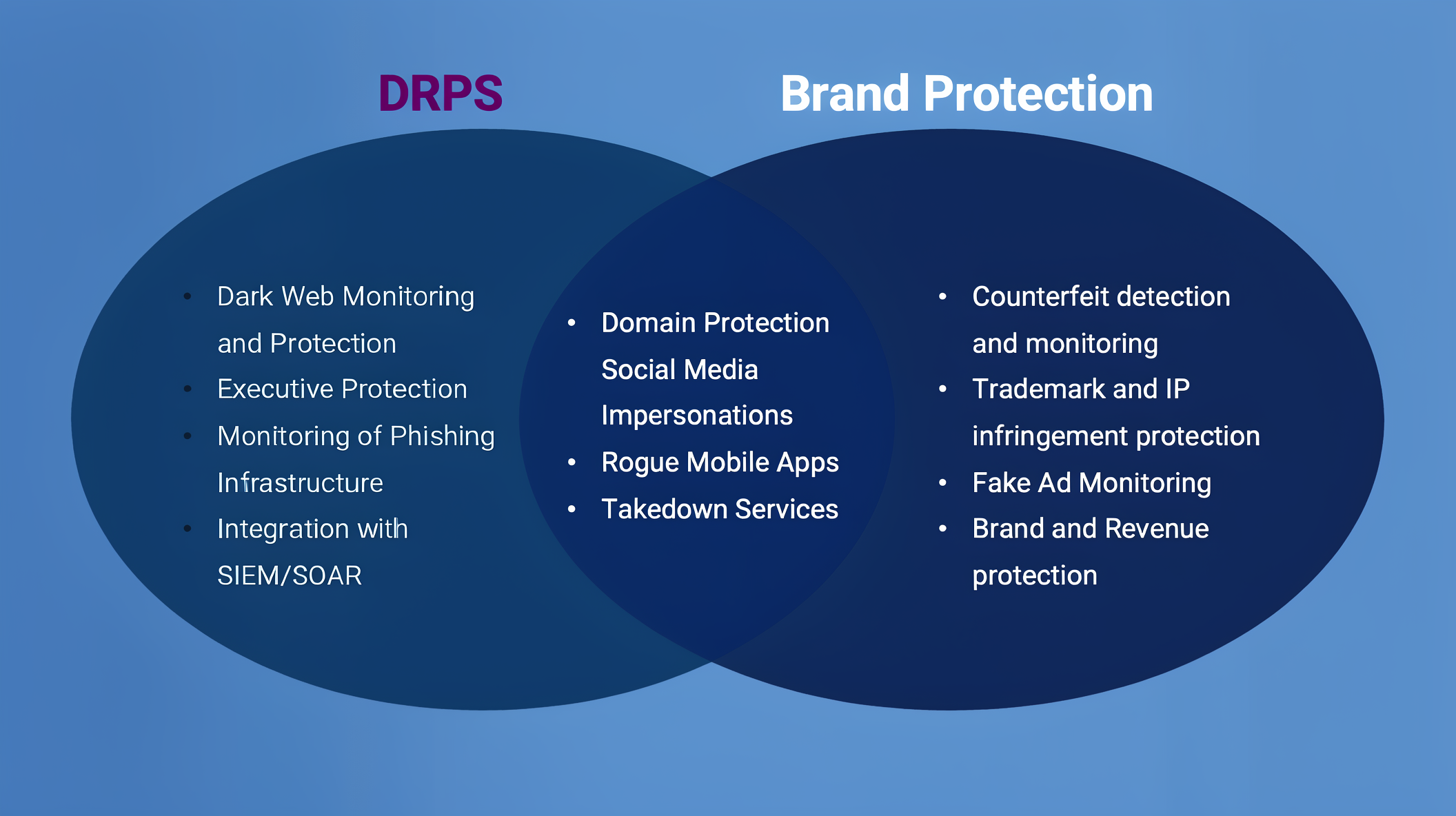
Partner with security experts like PhishFort for real-time detection and takedown of fake accounts.
PhishFort’s Brand Protection Services identify and remove phishing pages, impersonation profiles, and malicious campaigns across social platforms.
For individuals and crypto users, our Nighthawk browser extension helps detect phishing attempts before they cause harm.
Learn more at PhishFort Brand Protection Services.
Conclusion
Cyber attackers rely on social engineering attacks because they exploit human behavior – the weakest link in cybersecurity. The goal of most social media based attacks isn’t just data theft; it’s control, manipulation, and disruption of trust.
As social platforms continue to grow, so will these threats. Proactive monitoring, technology, and expert intervention are essential to protect your brand and your users.
PhishFort offers the tools and expertise needed to stop phishing before it spreads. Protect your digital presence – request a demo today.