
Raw Signals. Real Insights. Instant Action.
PhishFort’s Dark Web Intelligence delivers enriched, real-time threat data collected from phishing campaigns, scam infrastructure, and impersonation attempts to give security teams the context they need to hunt, investigate, and disrupt attacks faster.
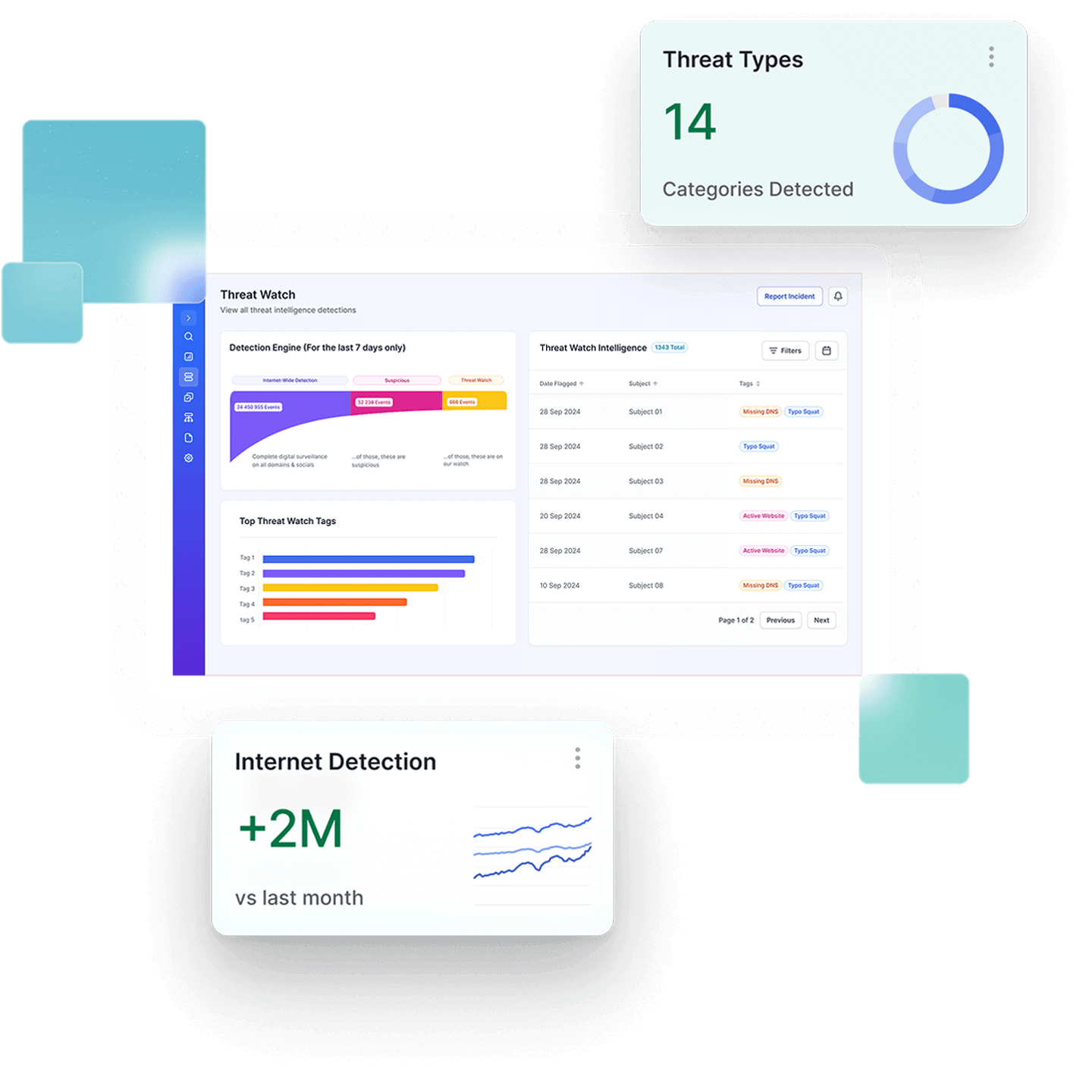
From Global Threat Activity to Targeted Defense
Malicious Domains and Infrastructure
Dark Web Mentions & Precursor Signals
Threat Actor TTPs
Brand and Executive Targeting
Takedown Intelligence
Threat Intelligence Built for Threat Hunters
Multi-Source Collection and Enrichment
Real-Time Feed Delivery
Operational Takedown Visibility
Scam and Infrastructure Clustering
Complete Digital Risk Protection – Wherever Threats Emerge


Fake App Detection & Removal

Brand Impersonation Monitoring

Threat Intelligence & Monitoring
Unmatched Capabilities. Proven Outcomes.
Takedowns
Monitoring
Detection
Why Leading Brands Trust PhishFort
The Gold Standard in Takedown
AI-Powered Threat Detection
Protection Across All Edges
Low-Touch Integration
Beautiful Visualization & Reporting
24/7/365 Coverage
Protect Your Brand and Revenue
Our advanced technology detects and takes down phishing websites, mobile app clones, and fake social media content.
See Why Customers Love PhishFort
Compared to previous period of time, it was 300-400 cases per year that were handled by us manually but [then] we saw 29,000 fake websites and domains were taken down by PhishFort service, which is really amazing. It was like 99.76% takedown success rate, which is really great because almost every fake website is taken down within something like 4-6 hours on average. This is something that we could not achieve by ourselves manually managing this process.
PhishFort has been incredible to work with. They do a fantastic job of protecting MyEtherWallet from a multitude of bad actors all over the internet. They are top tier and spring into action no matter the time of day (or night!). 10/10, will continue to work with PhishFort.
PhishFort has vastly improved how Spark can ensure it protects its users against fraudulent impersonators online. In the first eight months, they took down over 120 phishing domains and social media cases, with a 97% success rate. This prevented credential theft campaigns from spreading, and Spark saw a significant drop in successful account takeover attempts.
PhishFort has been a strong partner for Magpie, helping us monitor and remove phishing and impersonation attempts. Their work adds an important layer of protection that helps keep our community safer and more secure.
Seamless Client Communication and Tools for Enhanced Security
Private communication
Free browser plugin
The Dashboard
Trusted by the World's Biggest Brands










FAQs
Want to See PhishFort in Action?
See how PhishFort detects and eliminates digital threats across every digital space where your brand has a presence, with a curated demo tailored to your organization’s unique risk surface.