
Webinar: Stop Whack-a-Mole Enforcement
Join this live technical webinar to learn why domain-related takedowns often fail, what actually works, and how organizations can respond faster and more effectively.
Read moreStay informed with our latest blog posts.

Join this live technical webinar to learn why domain-related takedowns often fail, what actually works, and how organizations can respond faster and more effectively.
Read more
Key Takeaways Surgical Precision: 2026 supply chain attack news highlights a shift from mass infection to …
Read more
In today’s digital environment, logos represent far more than visual design — they embody customer trust. However, …
Read more
The internet is a vast landscape, and for many brands, it represents a blind spot as vast as the web itself. As we …
Read more
Navigating the job market in the Web3 and blockchain space has become a digital minefield. As developers increasingly …
Read more
The rise of digital asset theft has birthed a secondary, equally predatory industry: the crypto asset recovery scam. For …
Read more
In the hyper-connected landscape of 2026, your brand is more than just a logo or a name – it is a digital promise of …
Read more
In the modern digital economy, trust is the most valuable currency. However, as we move into 2026, that trust is being …
Read more
In the high-stakes ecosystem of Web3 and venture capital, meeting requests have become routine. But threat actors – …
Read more
As organizations move toward 2026, the cybersecurity threat landscape continues to expand beyond traditional network …
Read more
Takedowns are a common part of the internet today, especially for those dealing with a compromised site. Companies and …
Read more
Fake login pages are one of the most common techniques used in phishing campaigns to steal credentials and compromise …
Read more
Mobile apps are a growing problem for brands and consumers alike. As mobile usage continues to dominate digital …
Read more
Typosquat protection has become a critical security requirement as attackers increasingly exploit small naming …
Read more
Addressing brand impersonation, scams, and fraudulent activity across social platforms has become critical for brands. …
Read more
How to avoid holiday scams is something most people only think about after they’ve already been targeted by fake deals, …
Read more
Digital risk protection services play a vital role in modern cybersecurity strategies. As attackers increasingly operate …
Read more
A fake social media profile is one of the most common tools used by attackers to exploit trust on digital platforms. By …
Read more
Cybercriminals exploit fake domains to impersonate legitimate brands through lookalike registrations. These malicious …
Read more
DRPS tools are a critical part of modern cybersecurity strategies as external threats continue to grow beyond …
Read more
Social media impersonation has become one of the most effective tactics used by attackers to exploit trust and …
Read more
Executive monitoring has moved from being a niche security capability to a business-critical requirement. As …
Read more
Impersonation is one of the fastest-growing forms of social engineering. Rather than attacking infrastructure, threat …
Read more
A web threat defense service is designed to protect organizations from malicious activity targeting their digital …
Read more
Digital threat protection has become a core requirement for organizations operating in an environment where attacks no …
Read more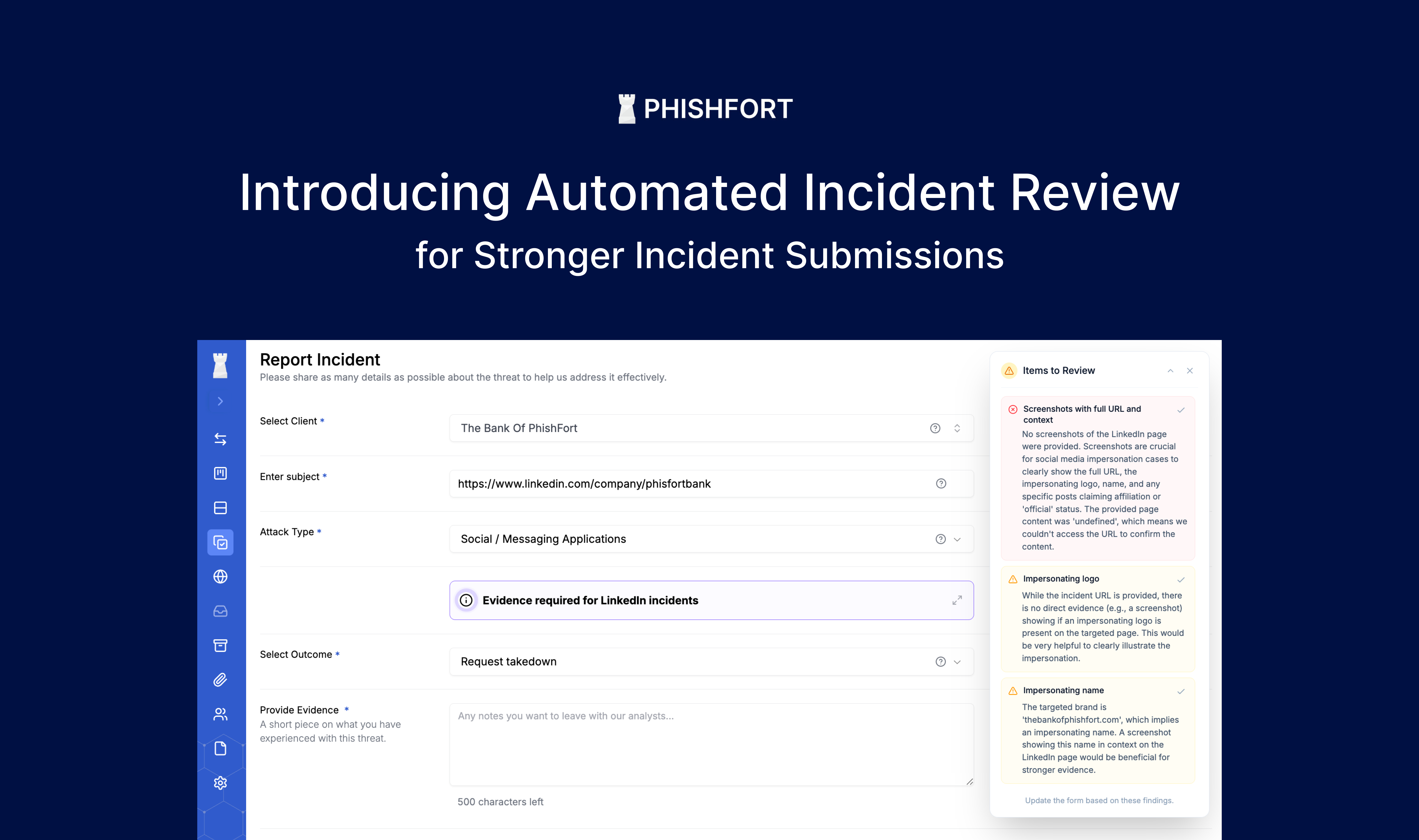
Built to Reduce Delays and Improve Takedown Outcomes Incomplete or unclear evidence is one of the most common reasons …
Read more
Takedowns are a common part of the internet today. Companies and individuals regularly seek to have harmful or …
Read more
The DMCA Takedown Guide provides a structured way to understand the Digital Millennium Copyright Act, how DMCA takedowns …
Read more
The Nuance of Takedowns is the title of a series created to highlight a reality that security teams experience every …
Read more
New Phishing Techniques continue to evolve, blending technical manipulation, deception, and platform-specific …
Read more
Crypto Phishing Scams continue to expand across Web3 ecosystems, targeting wallets, decentralized exchanges, recovery …
Read more
Why Hackers Target Gmail Users via Google Calendar Phishing Emails A new threat vector is rising fast – and this time, …
Read more
Domain suspension is a complex but crucial part of the modern internet. Companies and individuals regularly seek to have …
Read more
At the time of writing this, Amazon’s AWS experienced a massive outage in their US-East-1 region, disrupting everyday …
Read more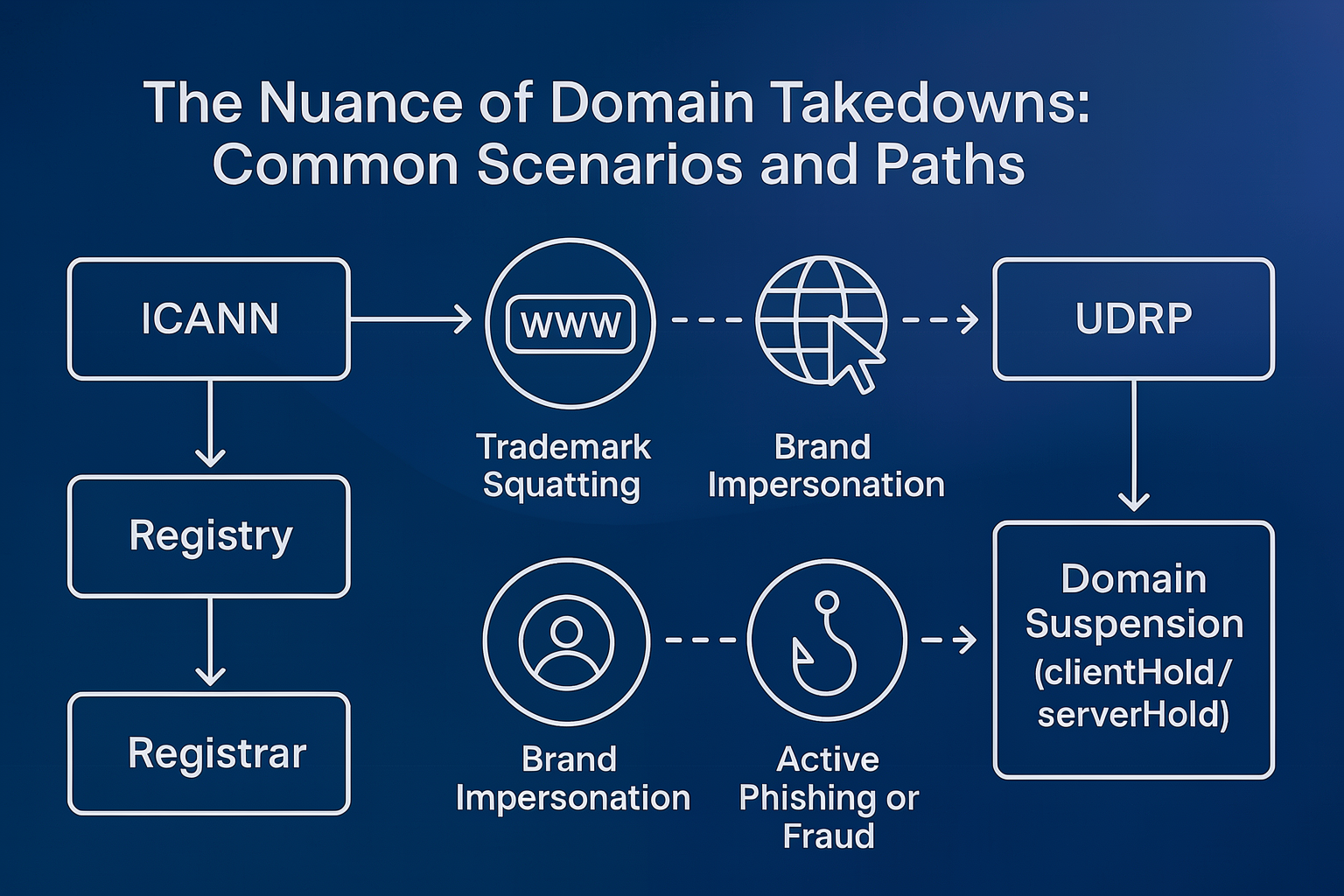
Takedowns are part of the internet’s plumbing. People want harmful or unauthorized content removed, but the path …
Read more
Release Date: 2025-10-14 Version: 1.0 Summary This release introduces PhishFort’s new Dark Web Monitoring module …
Read more
By Lucas Sierra, CEO at PhishFort Why We Built This When trying to keep your company and ecosystem safe, silence can …
Read more
Bitcoin Core: A High-Value Target for Cybercriminals Bitcoin Core, the reference implementation of the Bitcoin protocol, …
Read more
In the digital world we live in, your brand is no longer just a logo. Your brand is your company’s reputation, …
Read more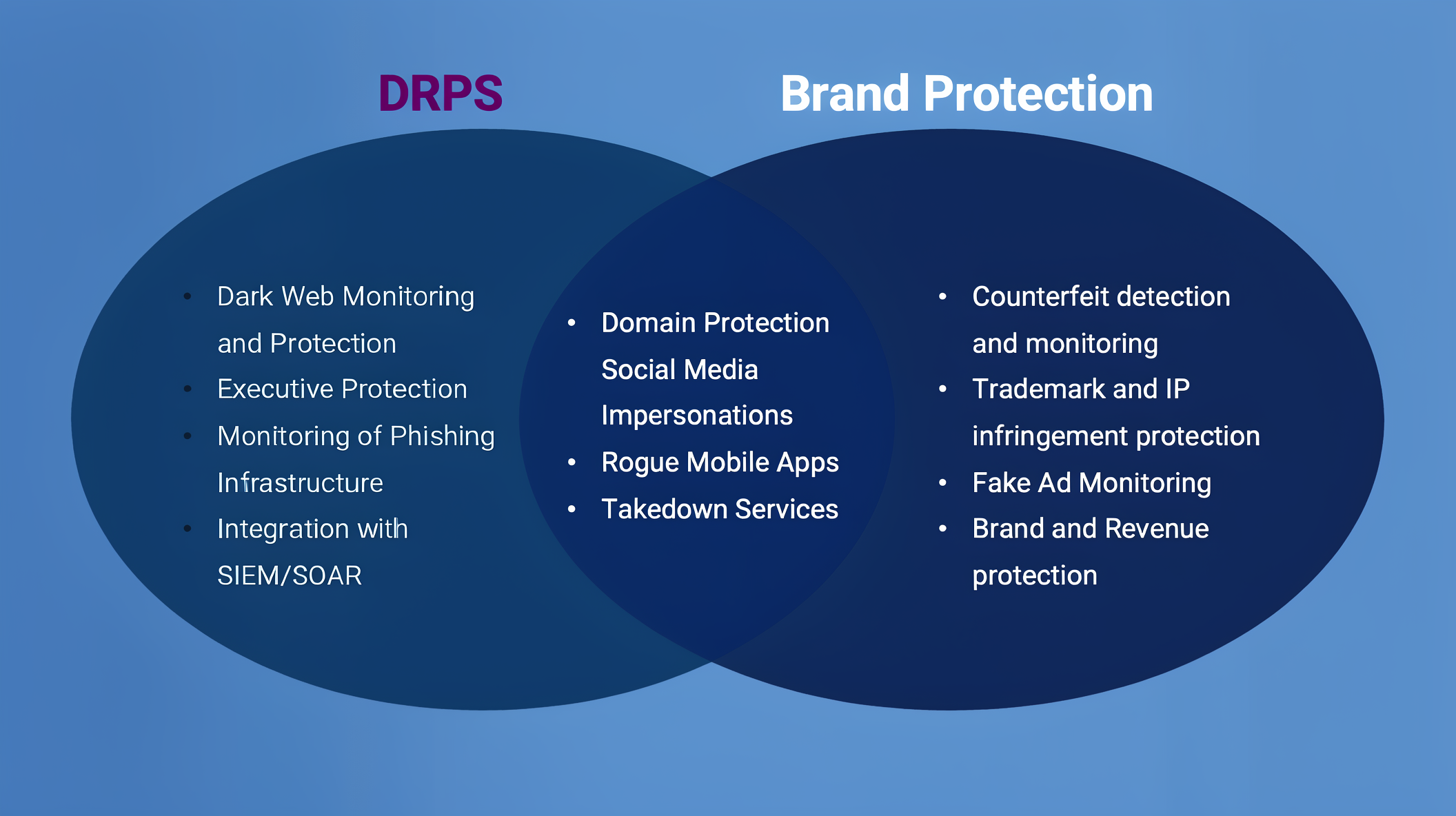
When security leaders and brand managers speak about “digital risk”, they may not be talking about the same thing. To a …
Read more
No single organization can see it all – by working together, we build stronger defenses for everyone. At PhishFort, we …
Read more
As cyber threats grow increasingly sophisticated, staying ahead of malicious actors has never been more crucial for …
Read more
Protecting your brand extends beyond delivering top-notch products and cultivating customer loyalty. Modern businesses …
Read more
What is Brand Abuse Detection? Brand abuse refers to the malicious exploitation of a company’s name, image, or …
Read more
At PhishFort, security isn’t just something we deliver for our clients – it’s a foundational principle that …
Read more
Phishing attacks have become one of the most pervasive threats to businesses of all sizes, across the globe. …
Read more
Brand protection, or what is brand protection, is no longer a simple task. Attacks from across the globe, using a …
Read more
Introduction The landscape of brand protection has fundamentally shifted. Today’s organizations face coordinated …
Read more
As cyber threats grow more sophisticated, organizations must combat phishing attacks that exploit brand trust. Attackers …
Read more
Safeguarding your online presence in today’s digital landscape is paramount, as cyber threats grow more …
Read more
While you are reading this, your brand is constantly at risk from online threats. Phishing attacks, impersonation, and …
Read more
Social Media Phishing Scams: How Cybercriminals Exploit Trust on Social Media Platforms Social phishing refers to …
Read more
Explore the hidden dangers of Twitter’s ‘Cards’ feature in our comprehensive analysis, …
Read more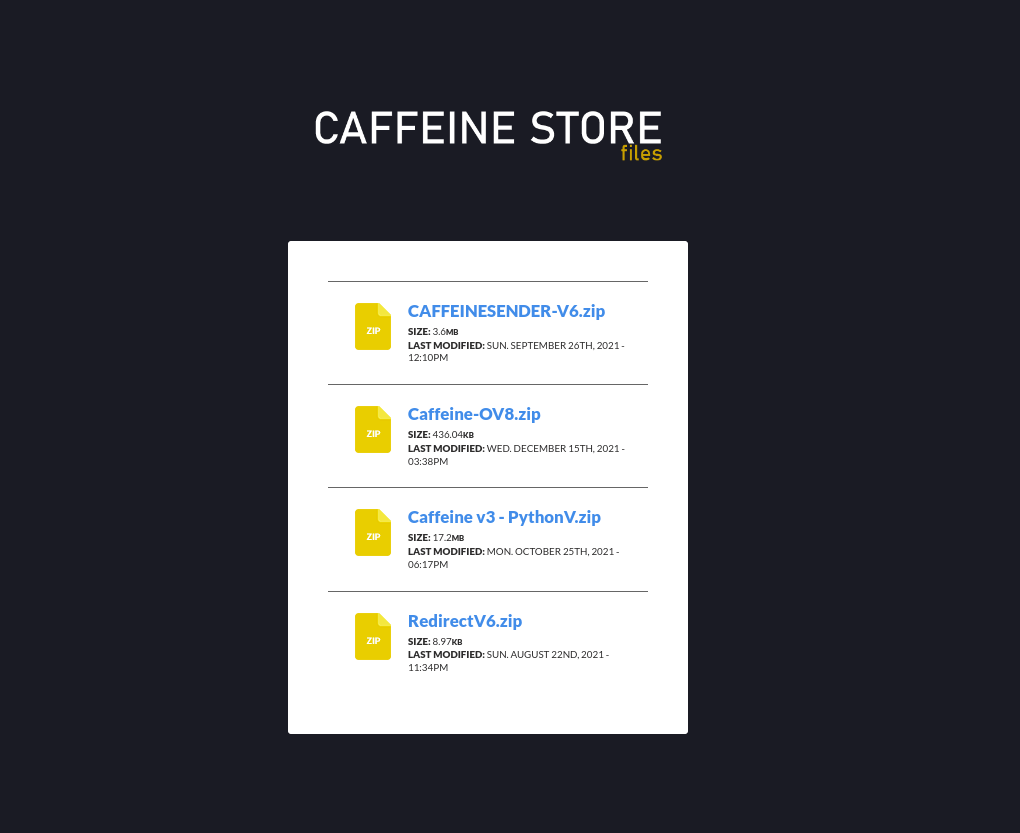
PhishFort recently identified a marked resurgence in Microsoft 365 credential-harvesting attempts, echoing tactics once …
Read more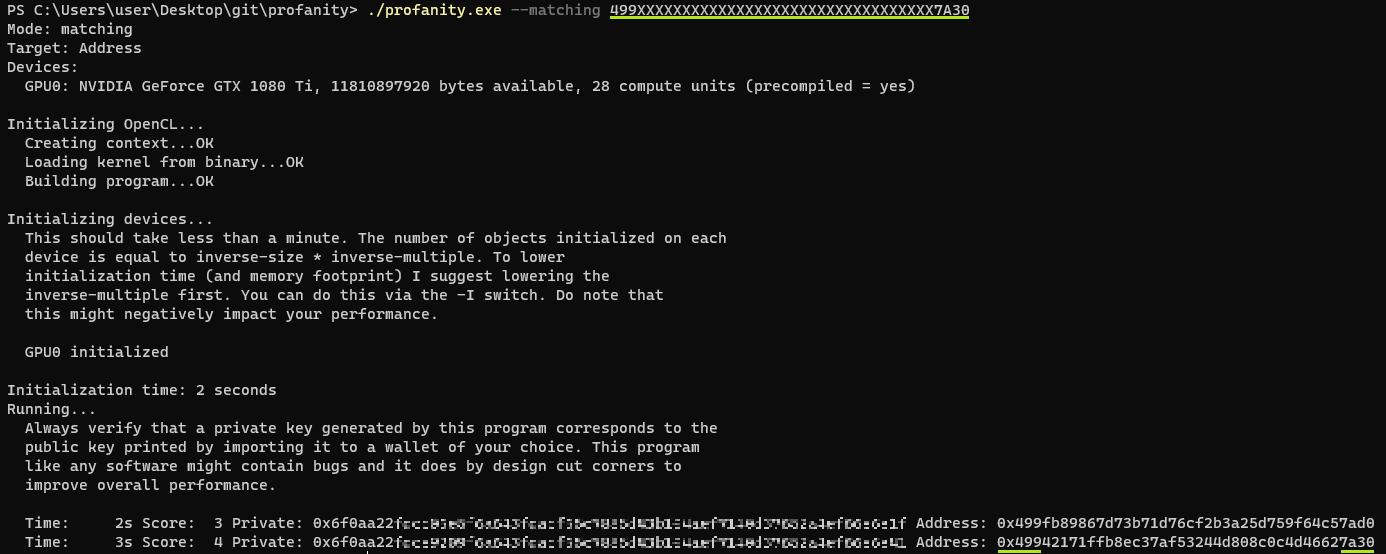
The United States Drug Enforcement Administration (DEA) fell prey to an address poisoning scam, losing $55,000 in …
Read more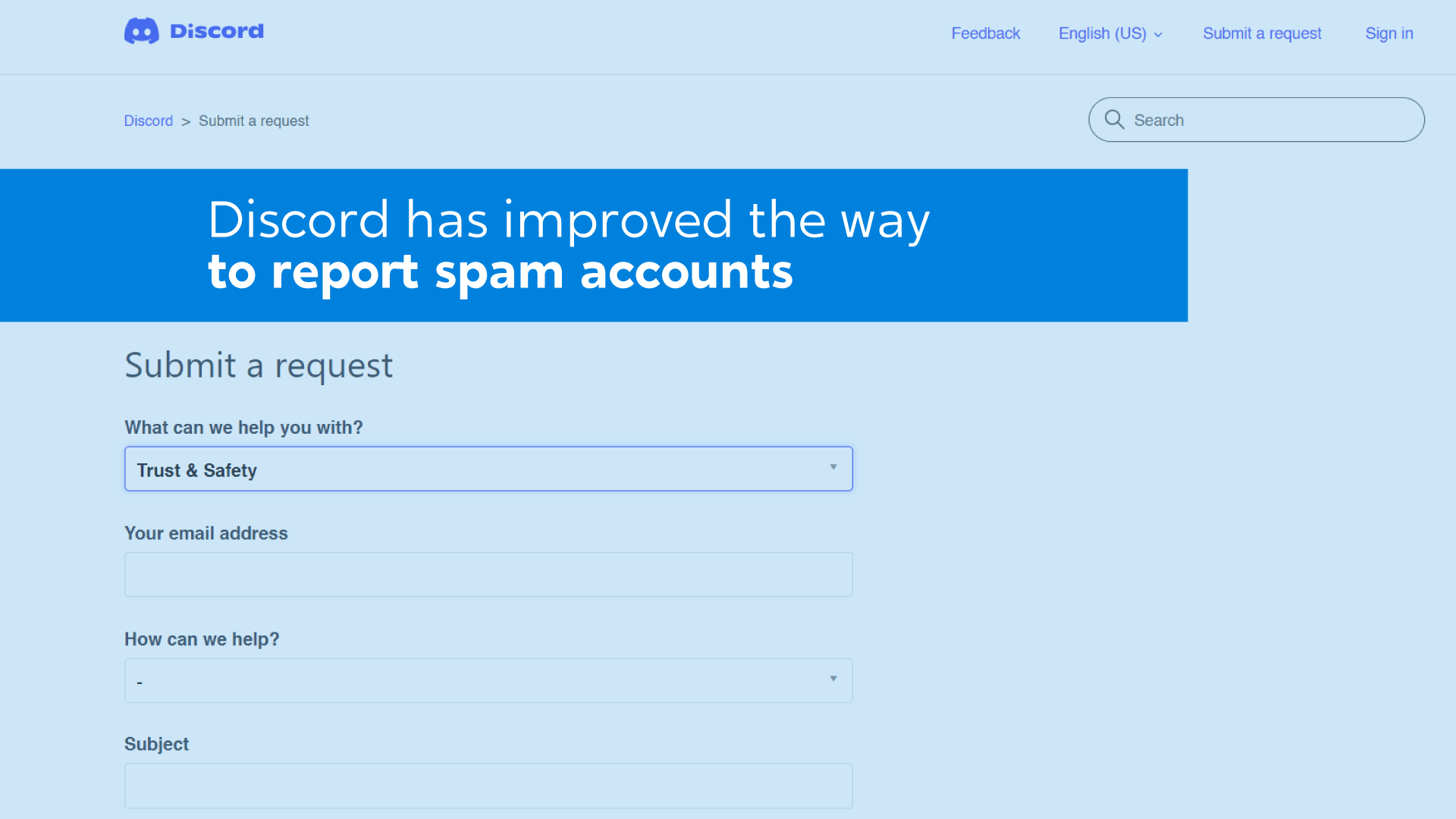
In the last few years, the use of the chat platform Discord has increased a lot. More than 150 million active users per …
Read more
Understanding Common Cryptocurrency Scams The rapid growth of digital assets has unfortunately brought a surge in …
Read more
DeFi (Decentralized finance) projects have exploded in popularity in the crypto industry over the past year. DeFi as a …
Read more
What Is Intellectual Property and How Is It Protected? You’ve just discovered that someone has copied your …
Read more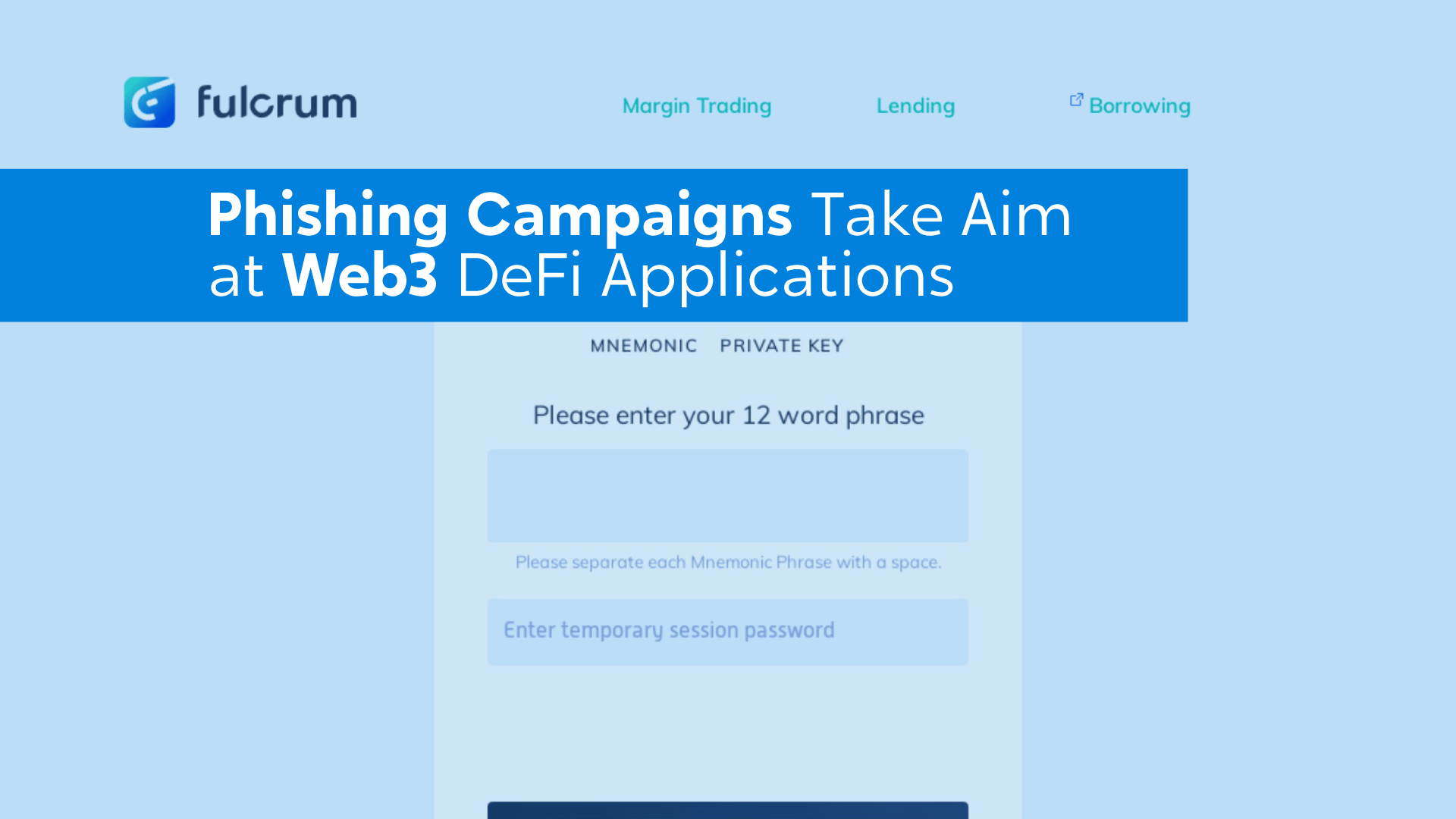
PhishFort.com and MyCrypto.com collaborated on this piece. This is the second collaboration piece with MyCrypto. In the …
Read more
One of the biggest challenges in cybersecurity today is keeping pace with phishing attacks. At PhishFort, our mission is …
Read more
The investigation was carried out by MyCrypto and PhishFort PhishFort has recently launched Nighthawk: an extension …
Read more
Working with cryptocurrencies is exciting for many reasons. Being on the cutting edge of financial technology, …
Read more
If you’ve ever searched Google for a copyright or trademark issue, you’ve likely come across the term DMCA. …
Read more
Why Cyber Attackers Commonly Use Social Engineering Attacks on Social Media The rise of social media has transformed …
Read more
It was only a matter of time before attackers pushed deeper into the crypto ecosystem. Web3 Domain phishing has now …
Read more
What Every Brand Owner Should Know You’ve invested time, creativity, and effort into building your brand. But when it …
Read more
2019 was a milestone year for PhishFort. As we look back, we’re proud of how our phishing protection solutions evolved …
Read more
“Hey, That Kinda Looks Like Mine?” – Learn how to identify, prevent, and take down copyright or trademark infringements …
Read more
Our early warning systems recently detected trustwället[.]com, an obvious phishing clone of the popular Trust Wallet …
Read more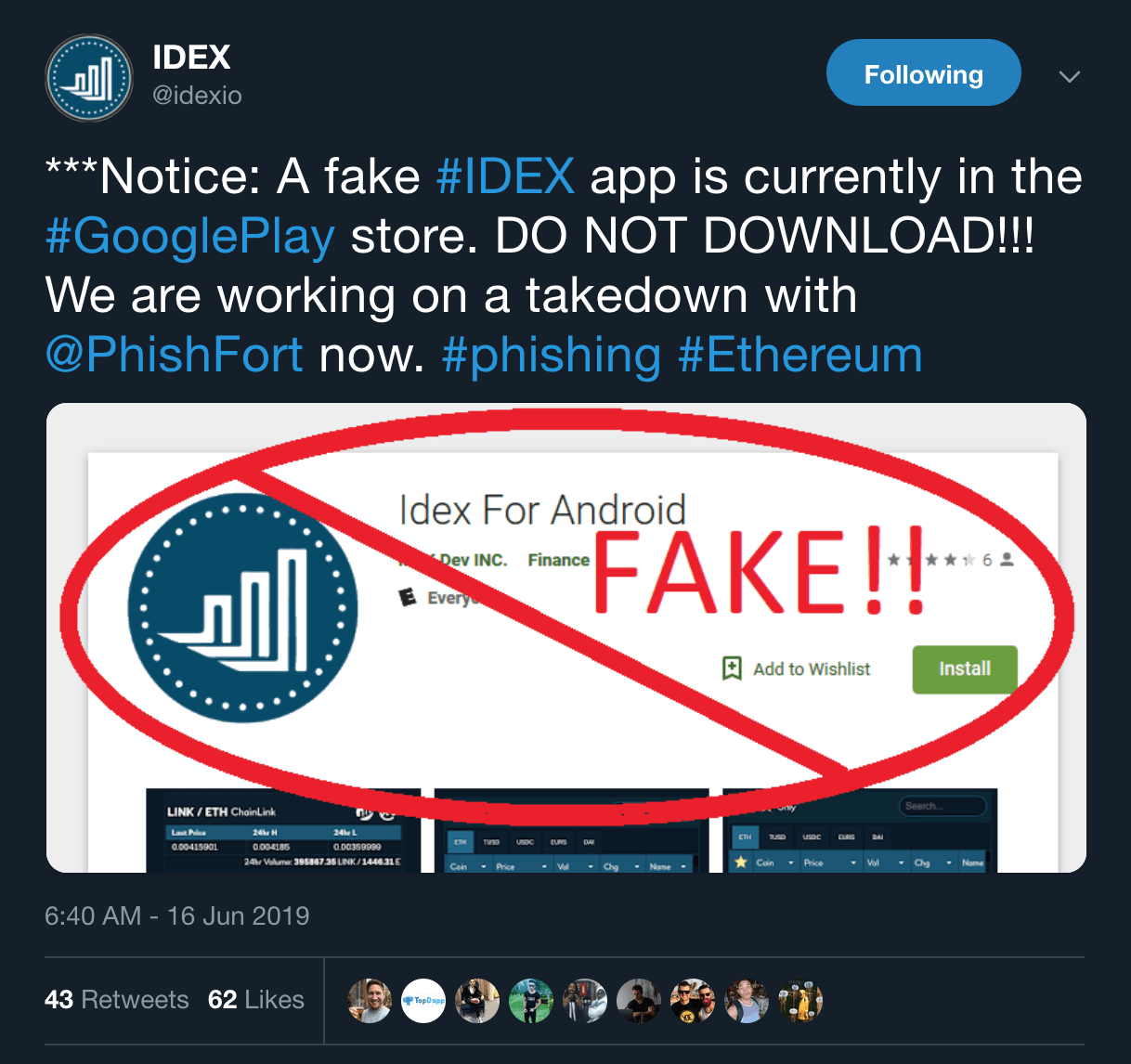
DEX Phishing attacks or Phishing attacks against decentralized exchanges (DEXs) are on the rise – and they’re …
Read more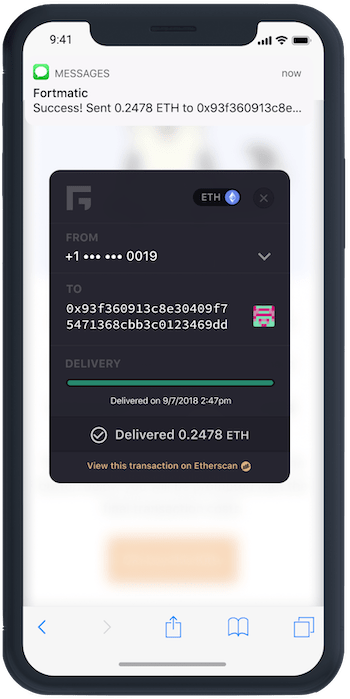
Fortmatic and PhishFort Team Up to Strengthen Web3 Security Fortmatic and PhishFort have joined forces to make the …
Read more
PhishFort and Binance Labs have officially partnered – and we couldn’t be more excited to share this next step in …
Read more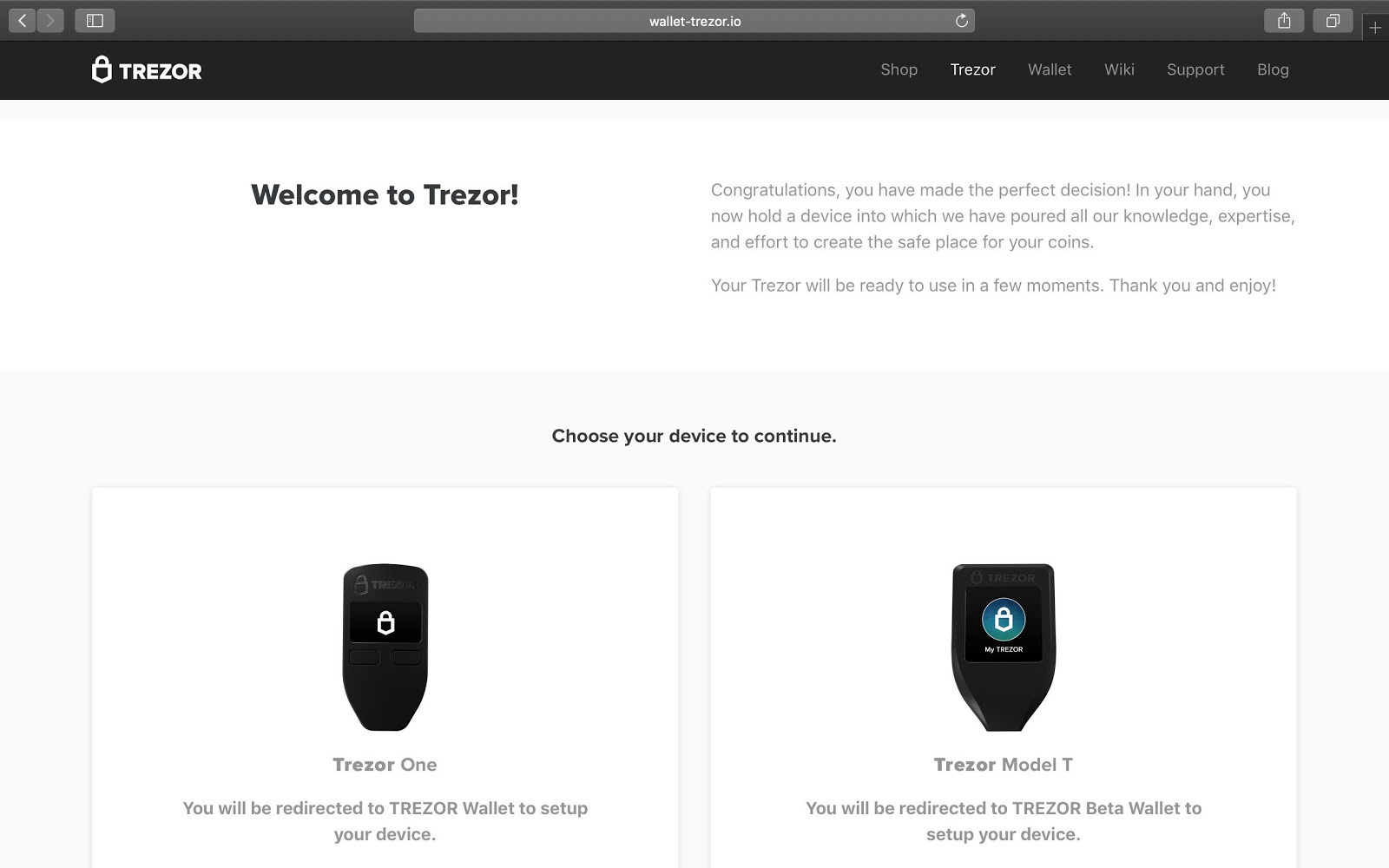
Can a Hardware Wallet Get Phished? Security remains one of the biggest barriers to widespread adoption of crypto. Within …
Read more
1. Know Your Senders Phishing attacks as emails often impersonate trusted organizations like banks or cryptocurrency …
Read more
PhishFort Team Up with Paxful PhishFort Partners with Paxful to Strengthen Cryptocurrency Phishing Protection PhishFort …
Read more
Research produced in conjunction with Oliver Hough. Binance is one of the world’s largest cryptocurrency exchanges so …
Read more
Research produced in conjunction with Oliver Hough. Binance is one of the world’s largest cryptocurrency exchanges …
Read more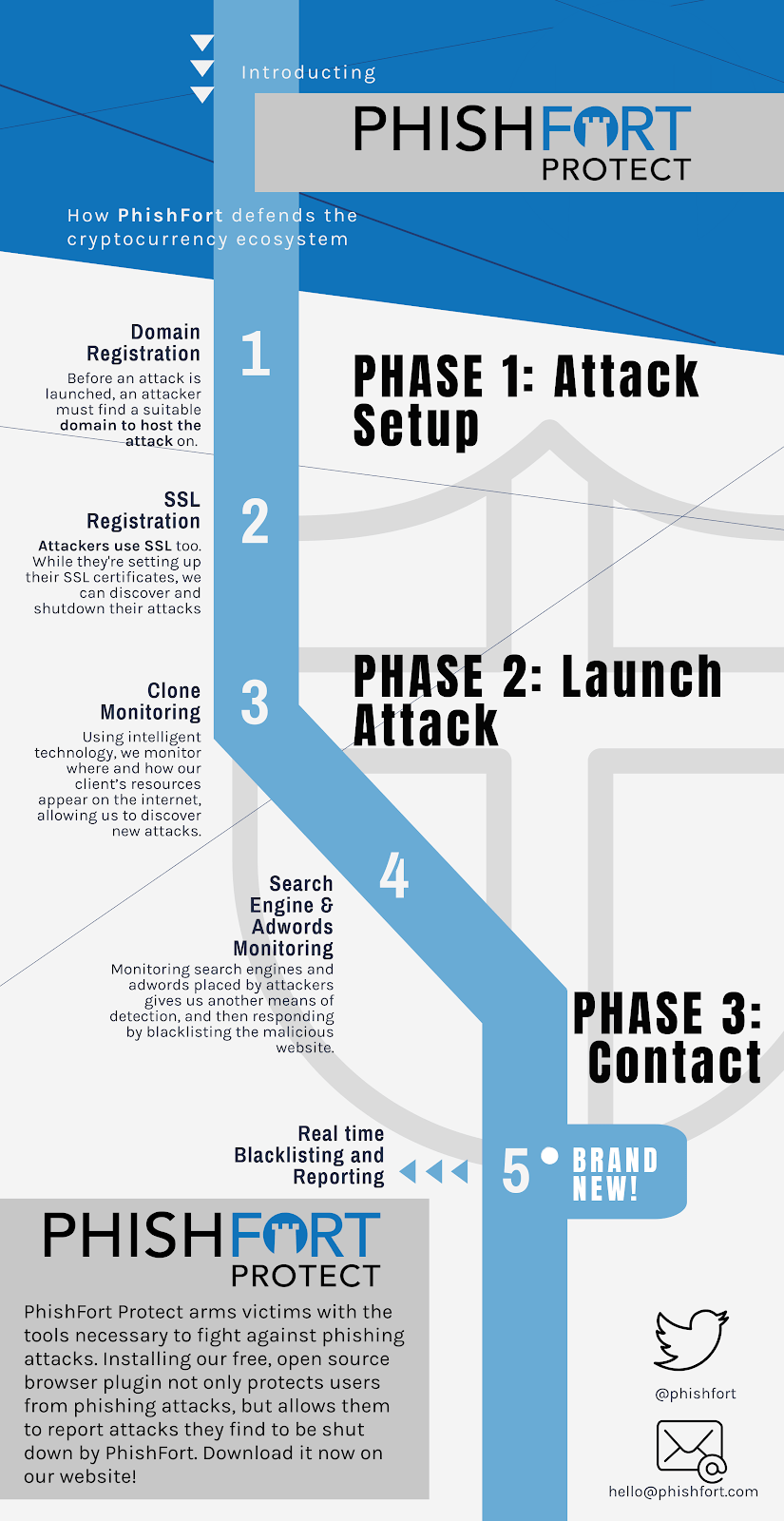
Introducing PhishFort Nighthawk: A Free Browser Extension Fighting Cryptocurrency Phishing The PhishFort Ecosystem …
Read more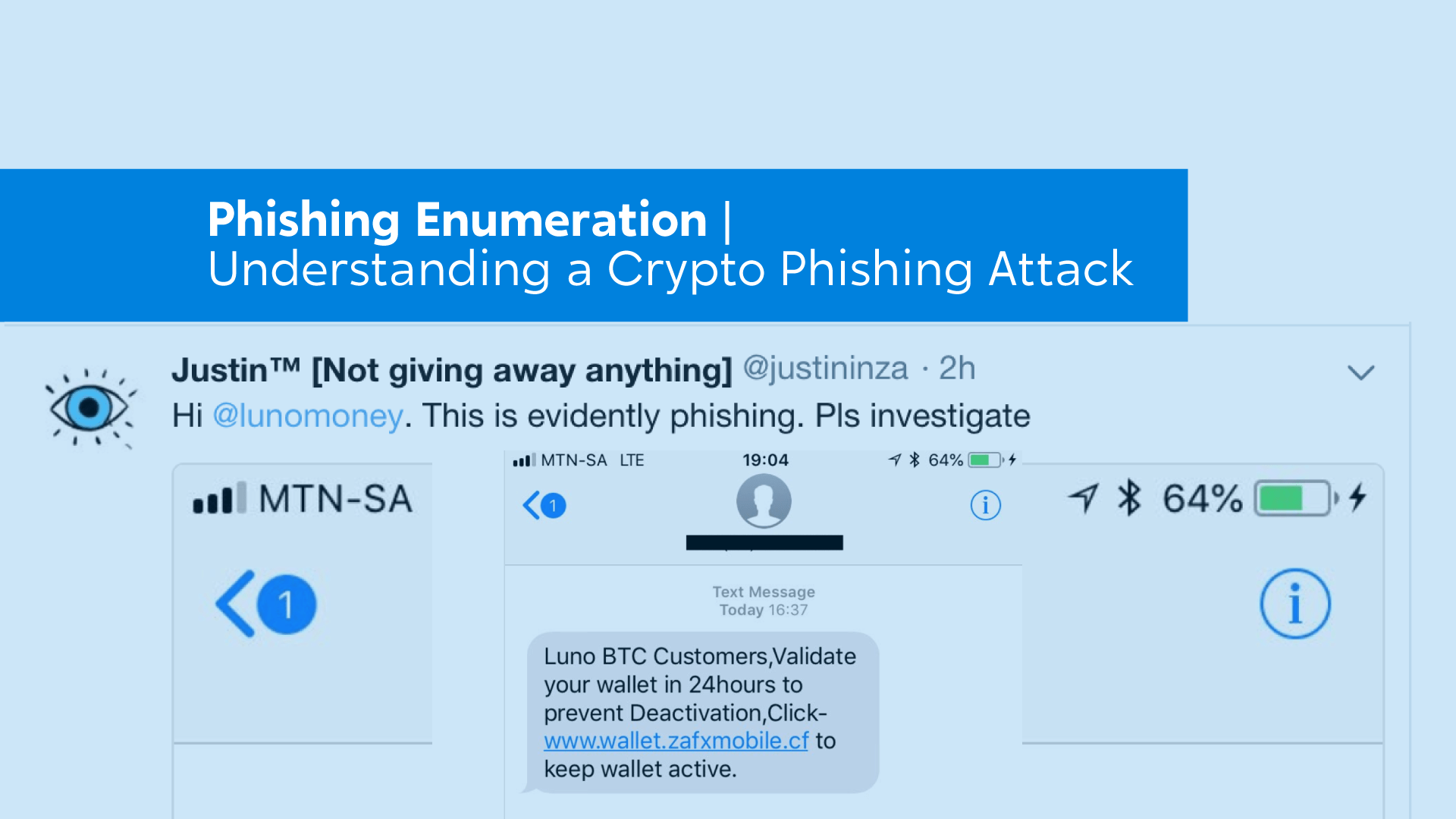
This is a brief exploration of an attack that surfaced one night and was reported on twitter against a user of the …
Read more
We’re excited to release the latest addition to our family of anti-phishing tools for the cryptocurrency industry. …
Read more
Our early warning systems recently detected a spike in Binance related attacks. Our analysts investigated the spate of …
Read more